Become a Member of Cyber Rescue for a bespoke Cyber Crisis Response Plan, for your organisation. During a cyber attack, call us for succinct advice. Click images for each report. (Or go to Threat analysis, attack maps, response guides, quotes, jokes, LinkedIn or Twitter.)

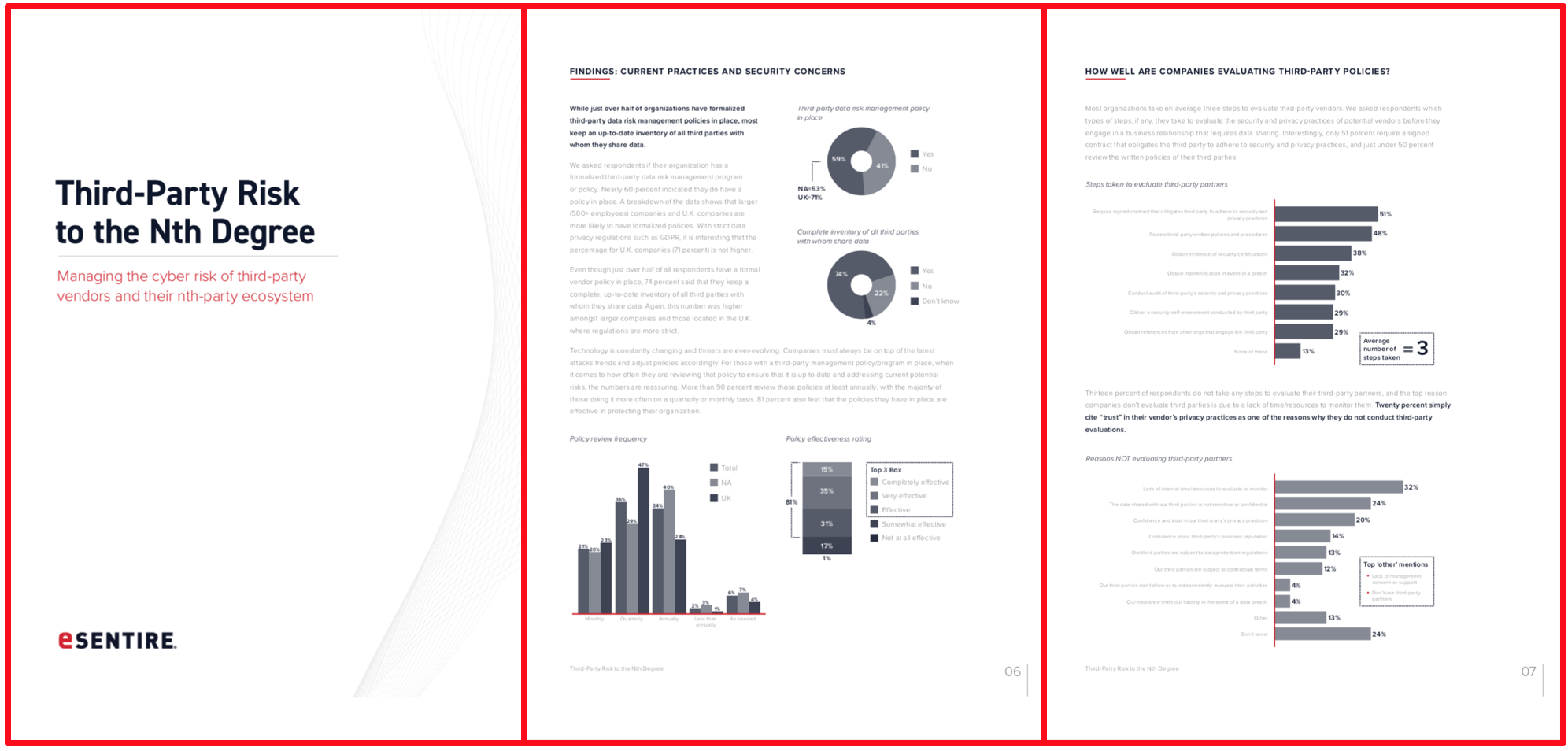

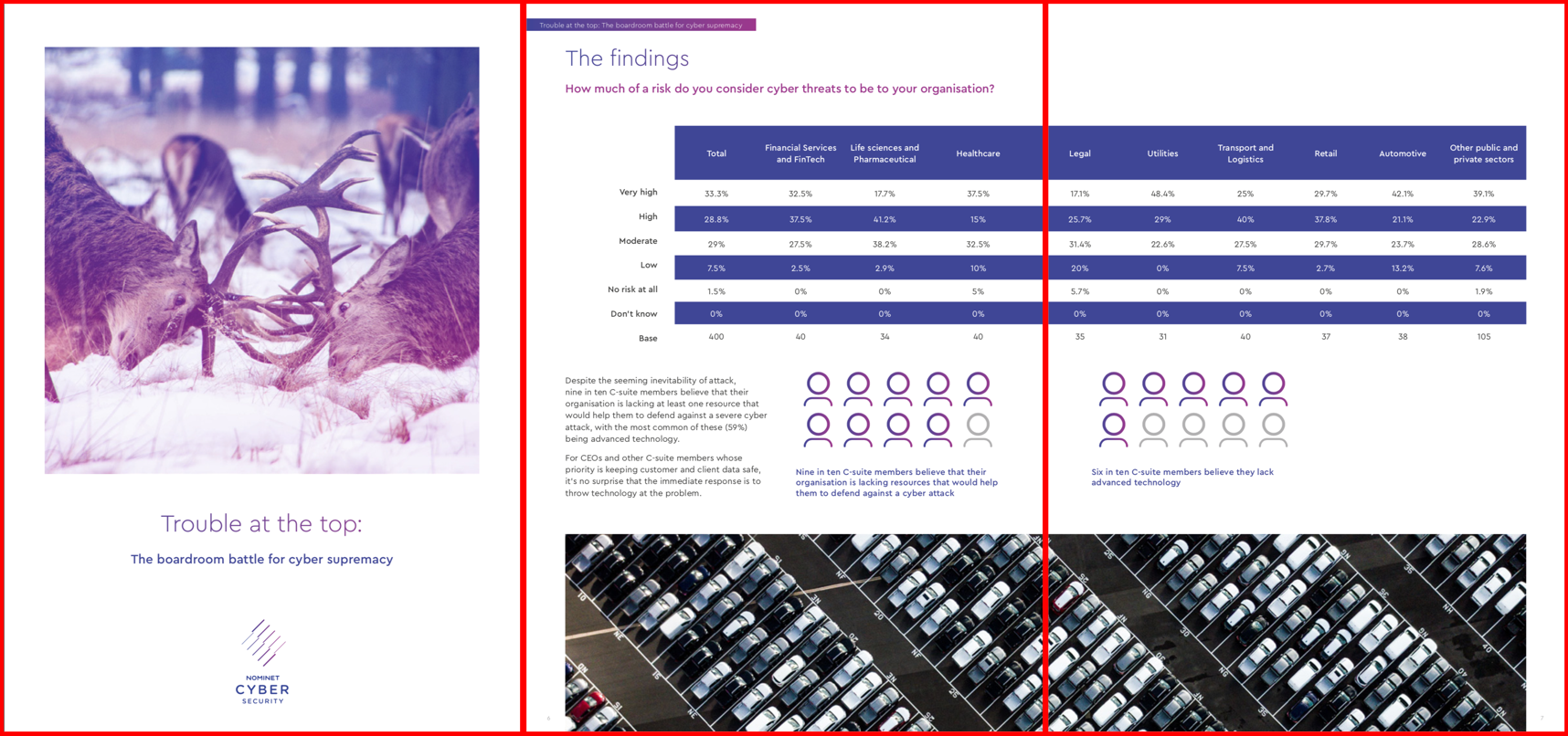
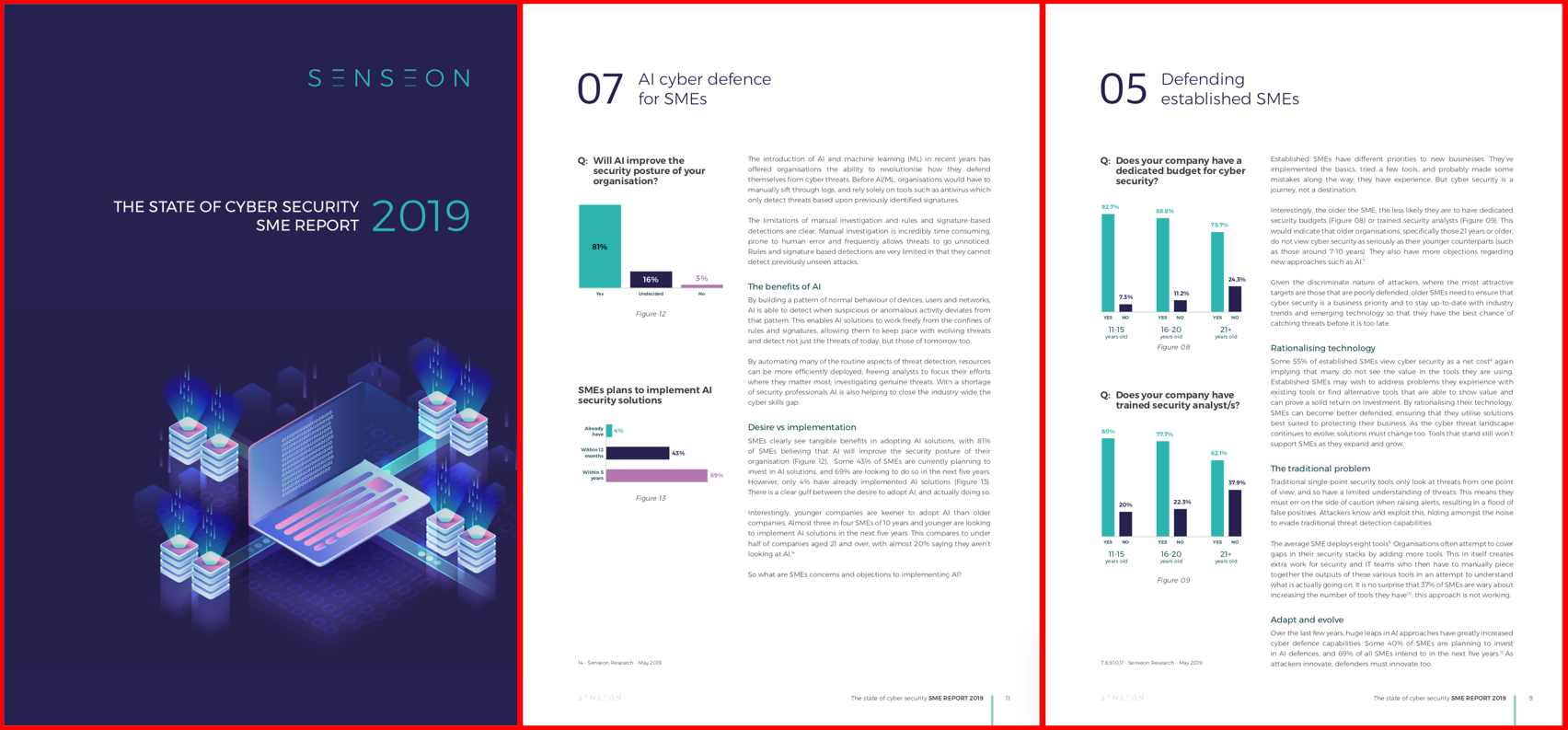
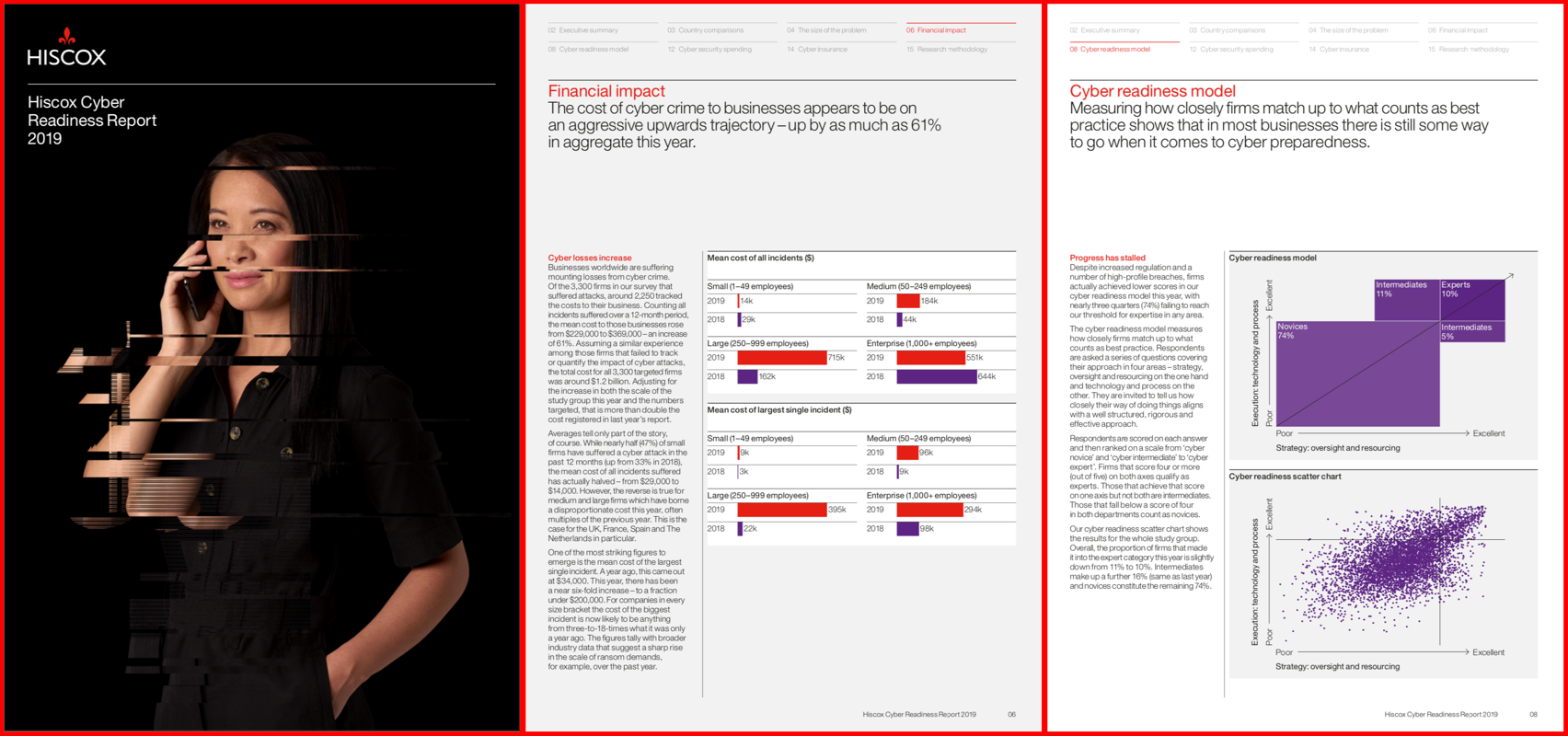




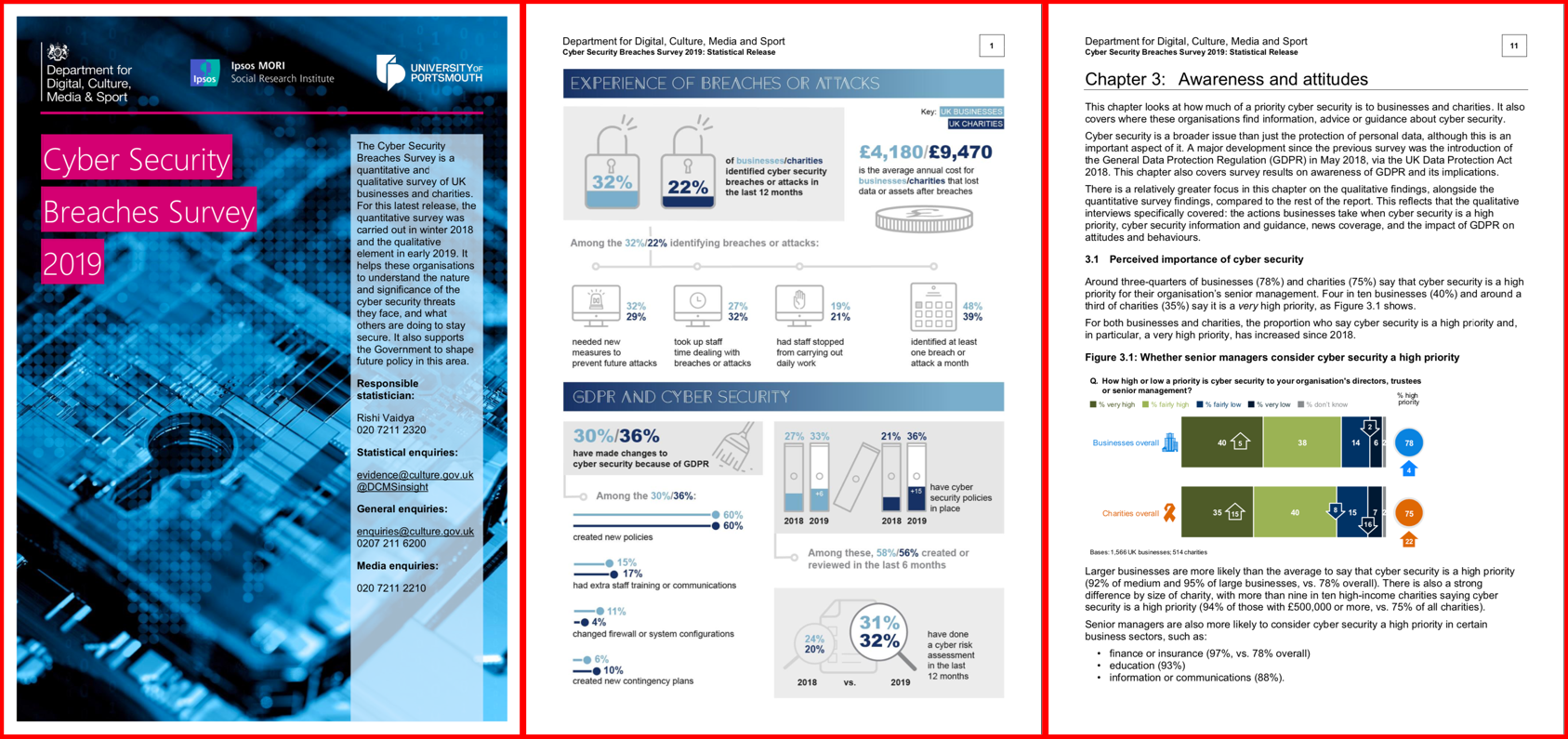
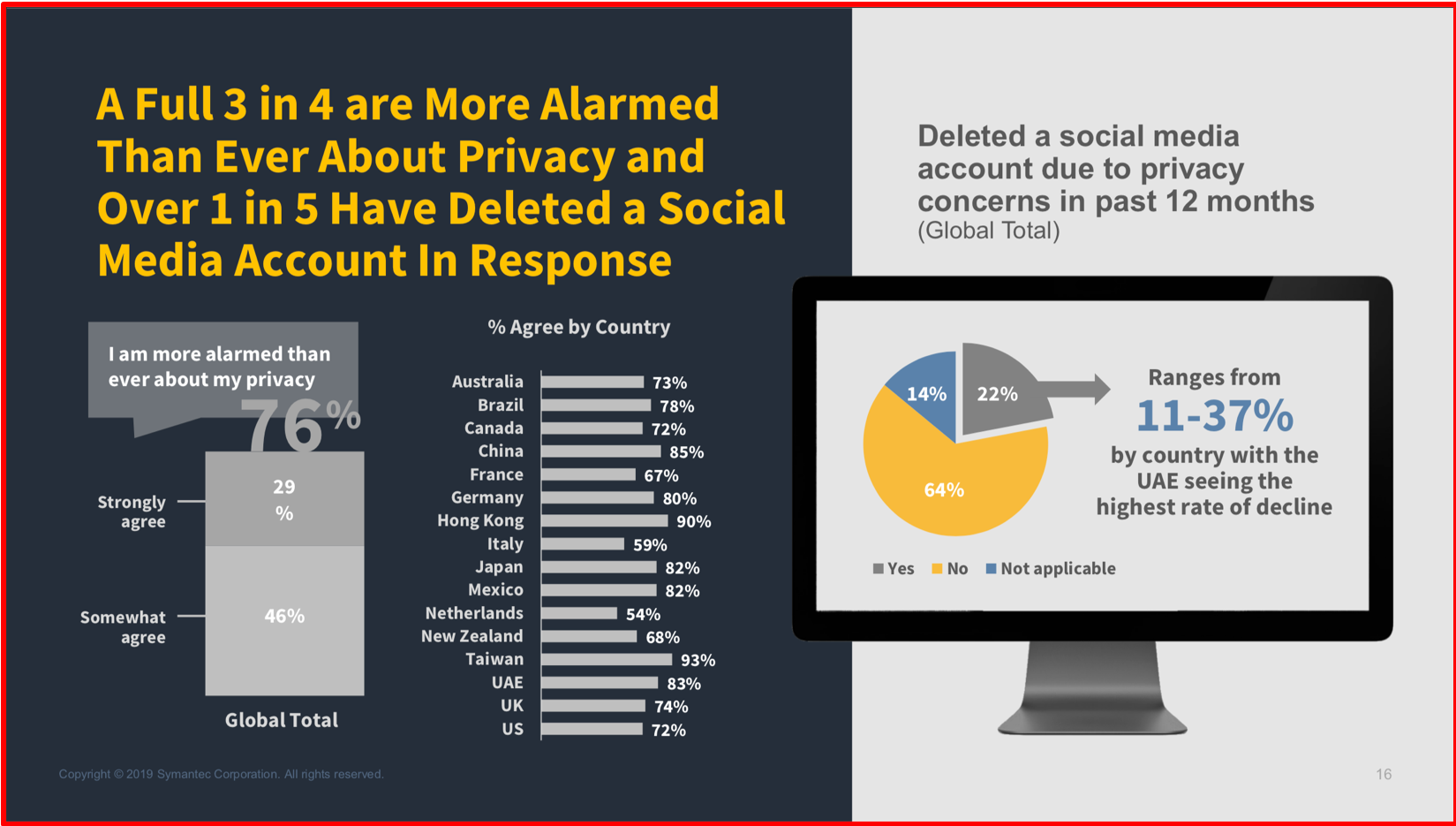
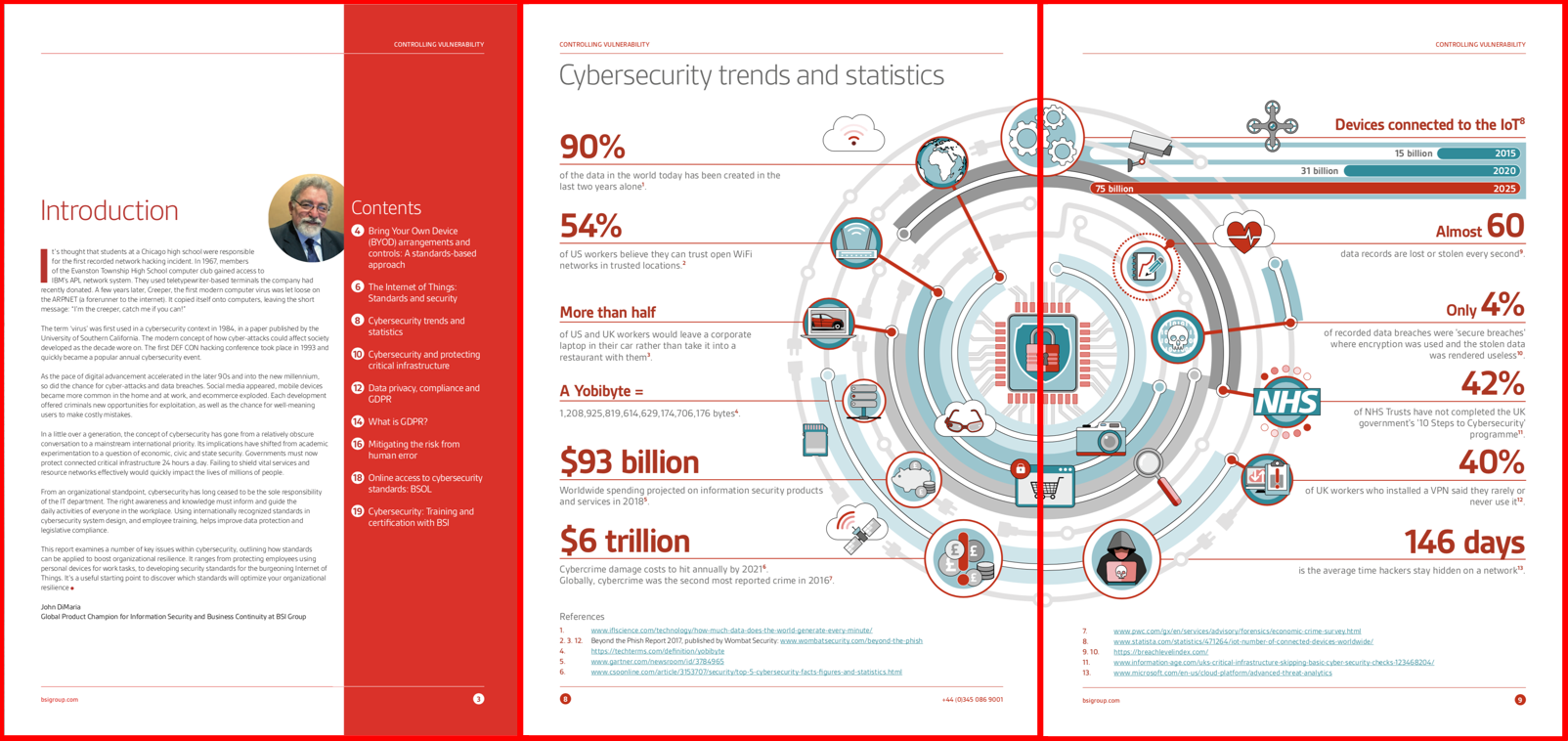
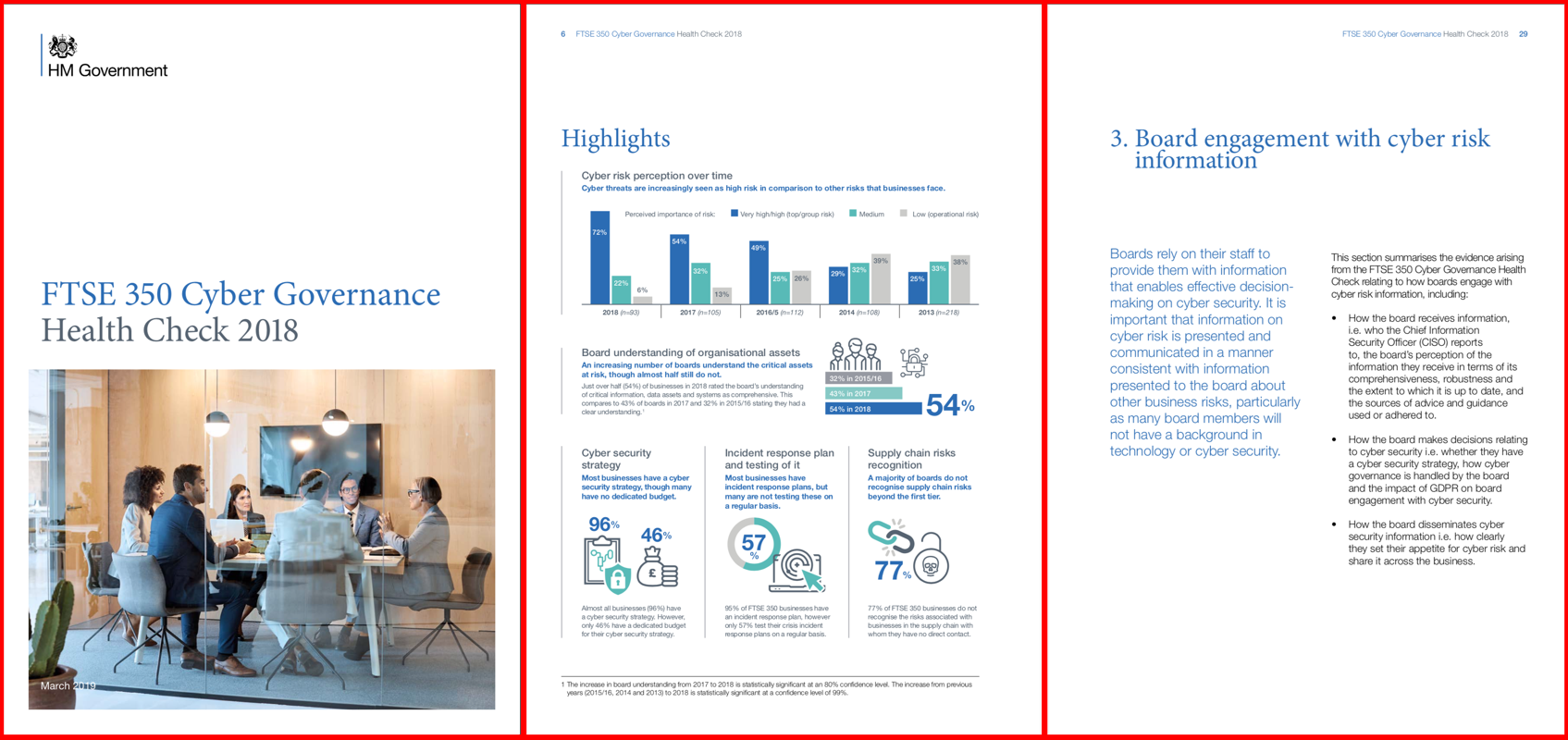






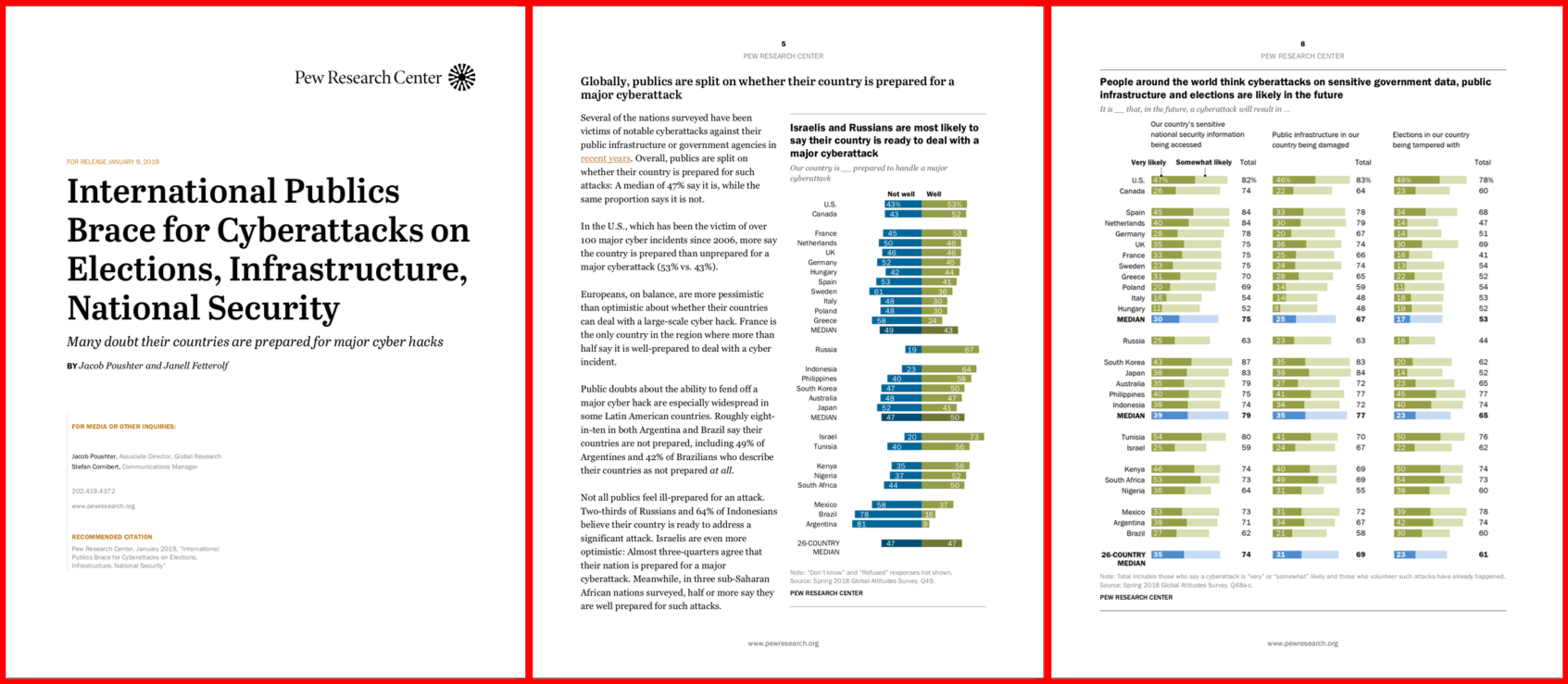


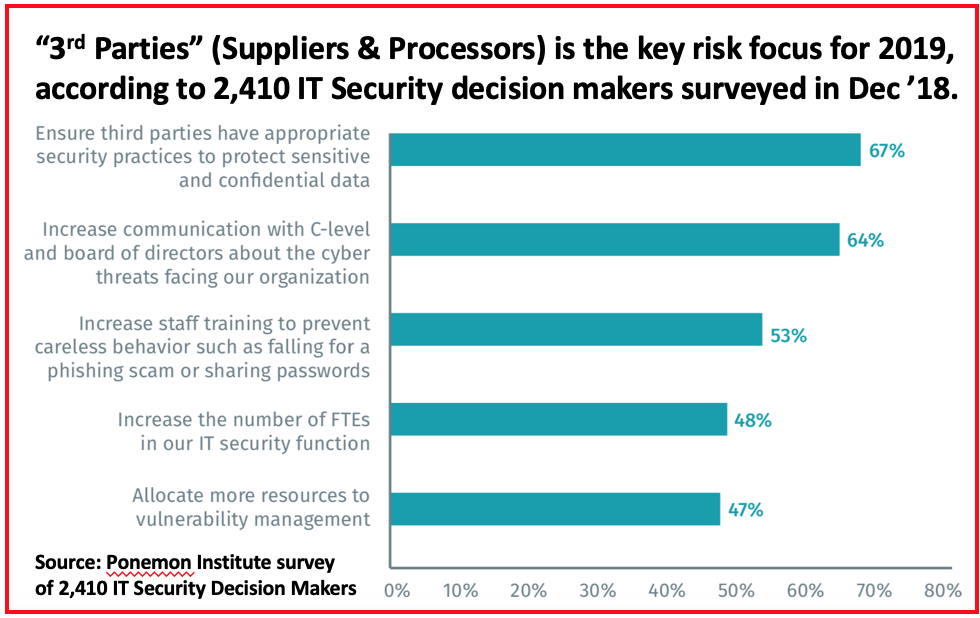
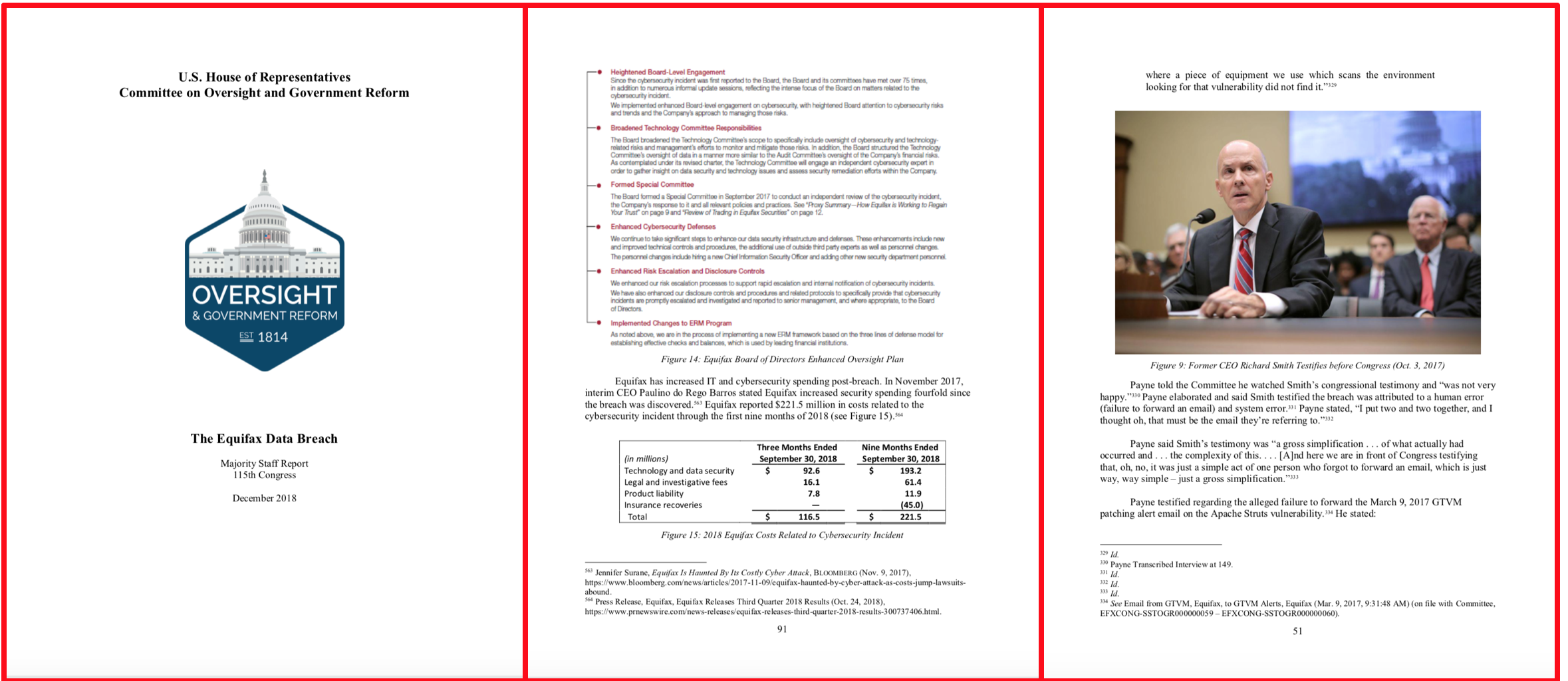



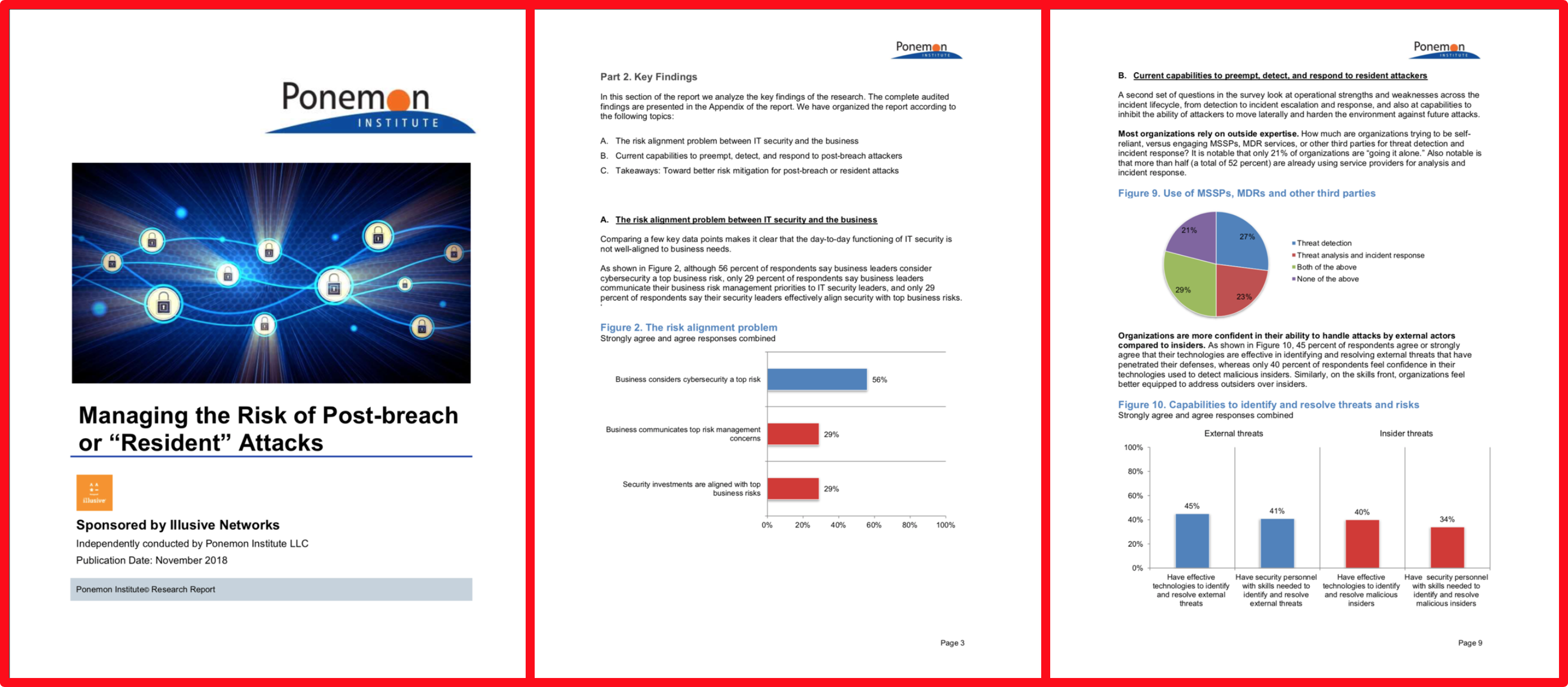
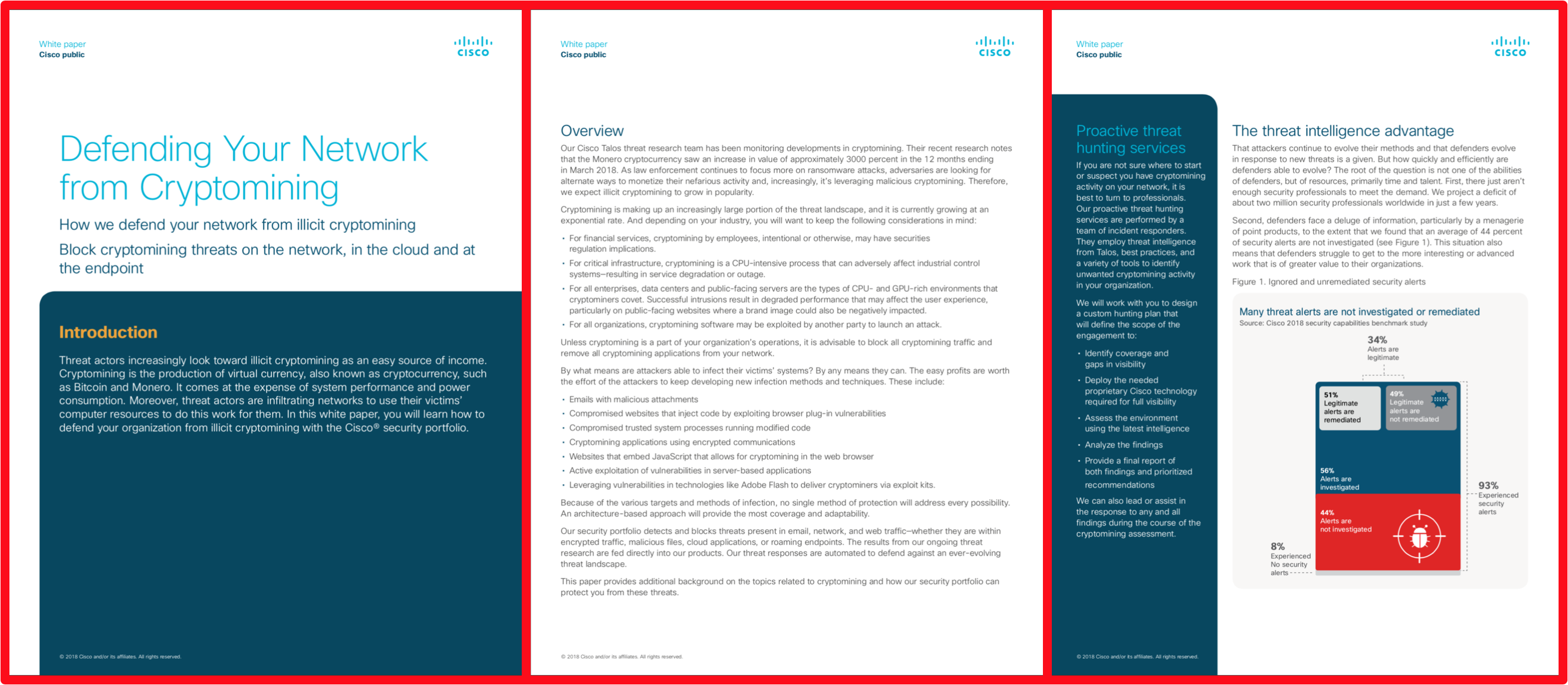
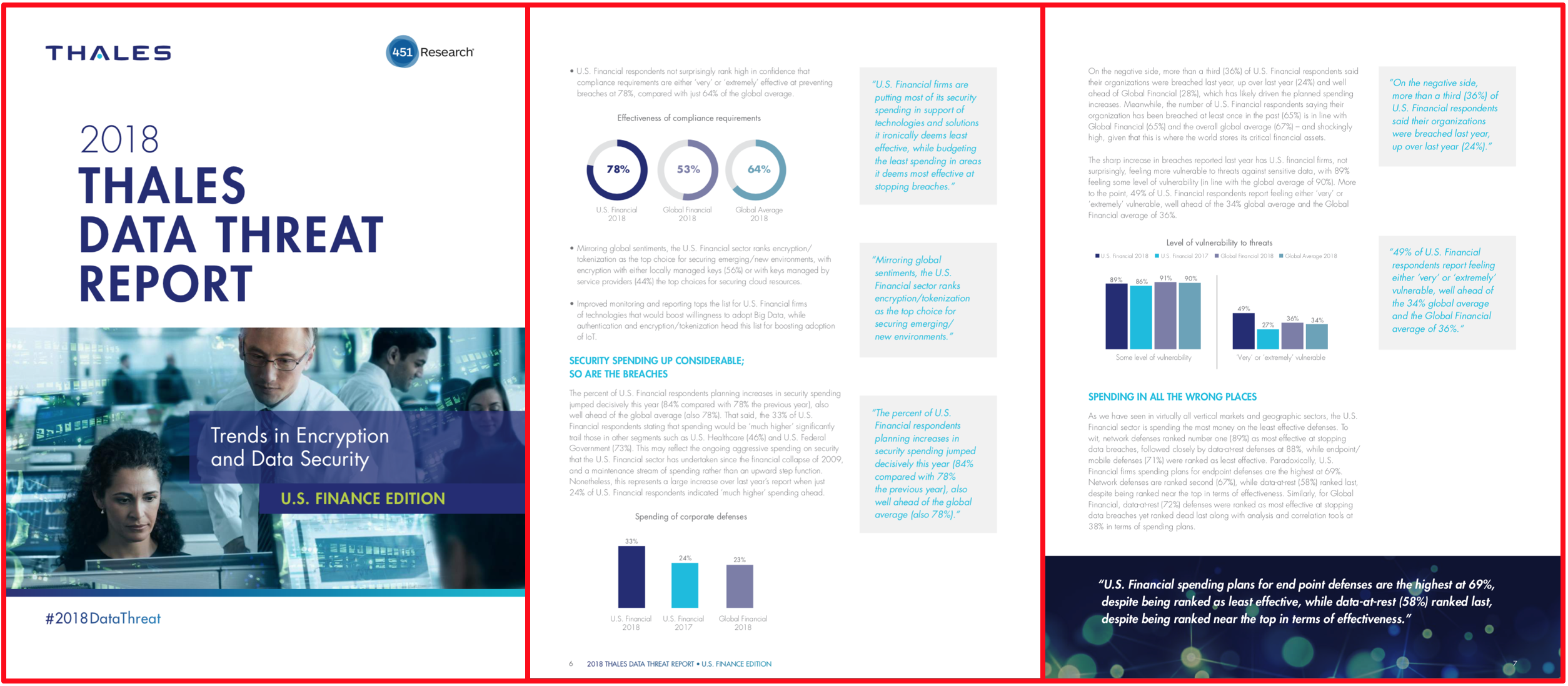












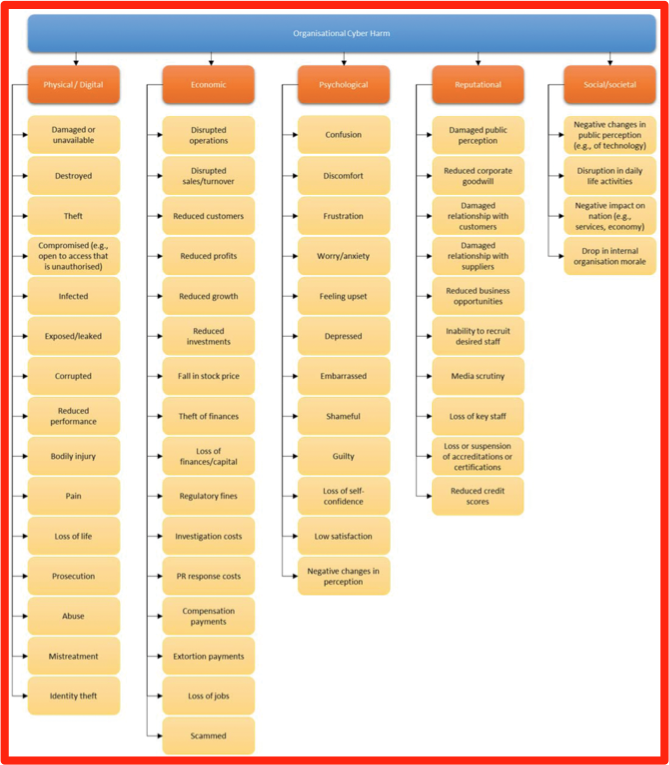

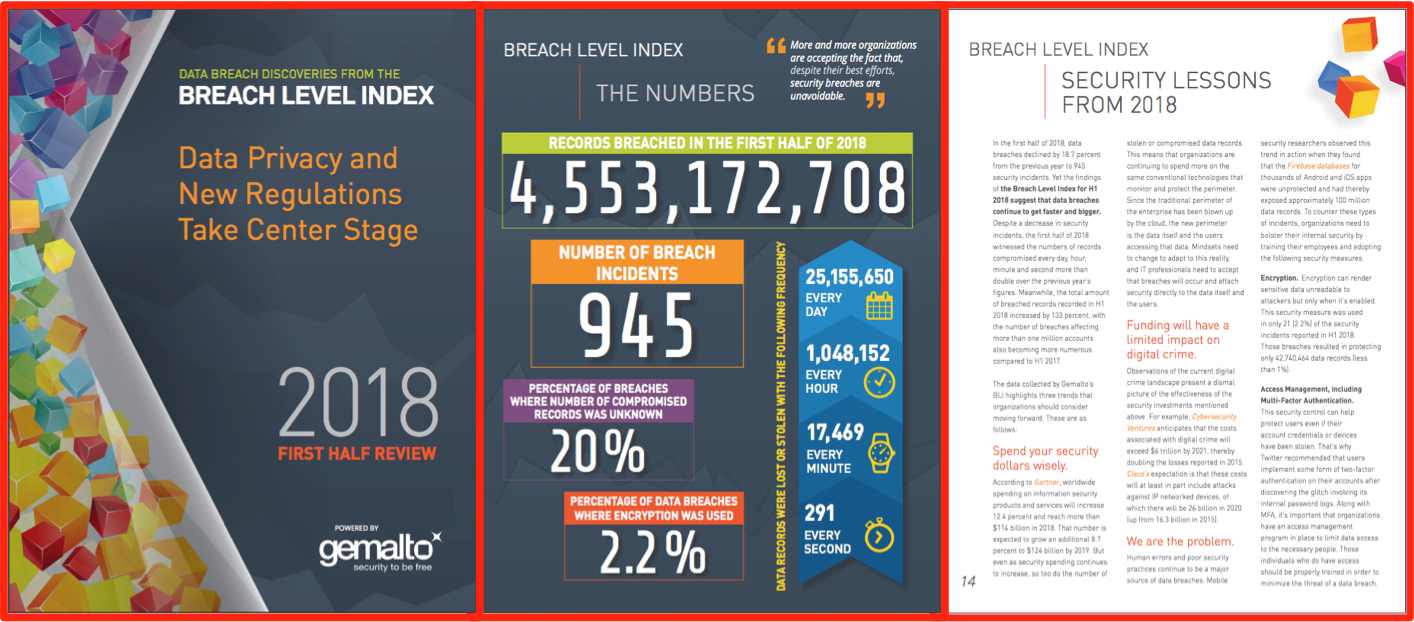
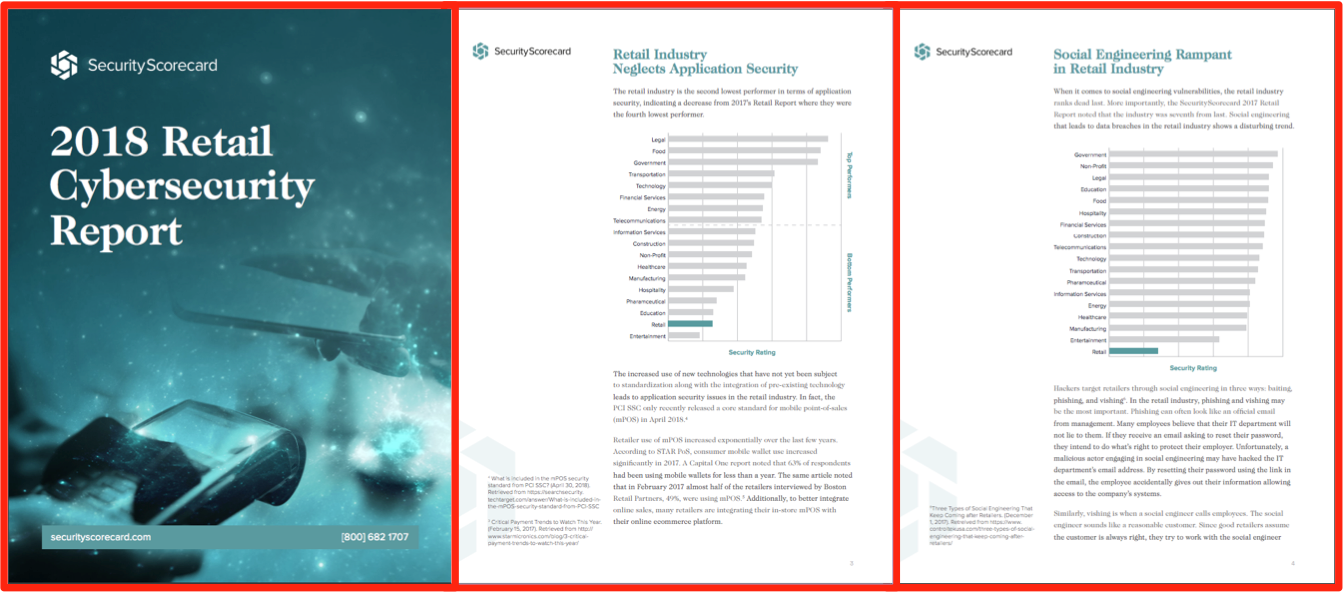
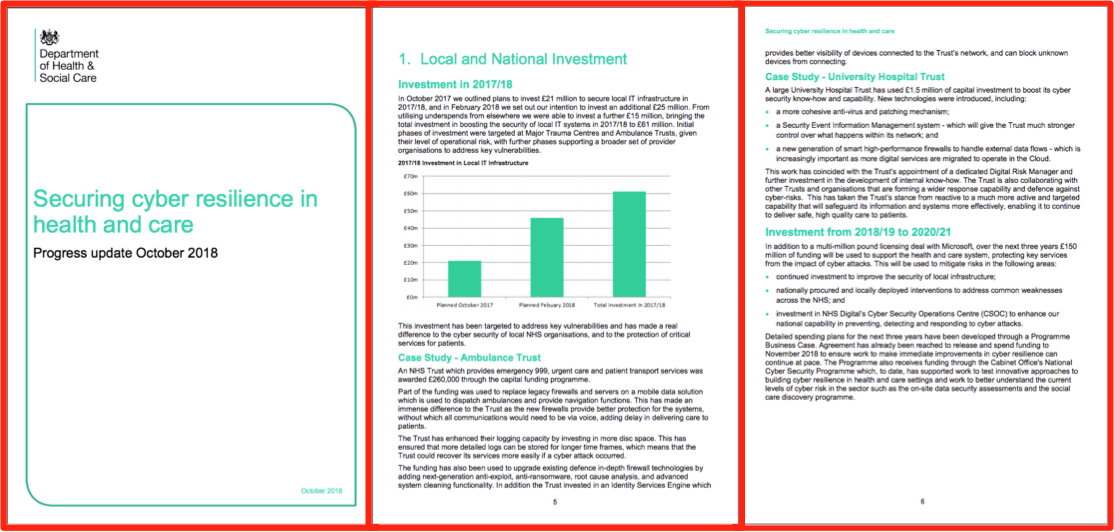


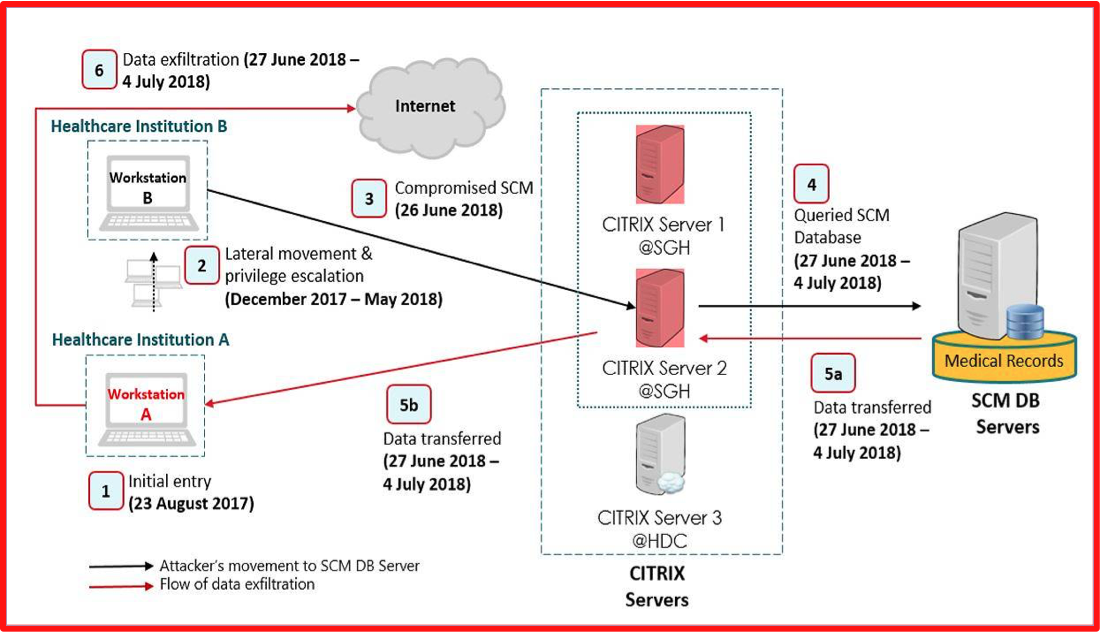
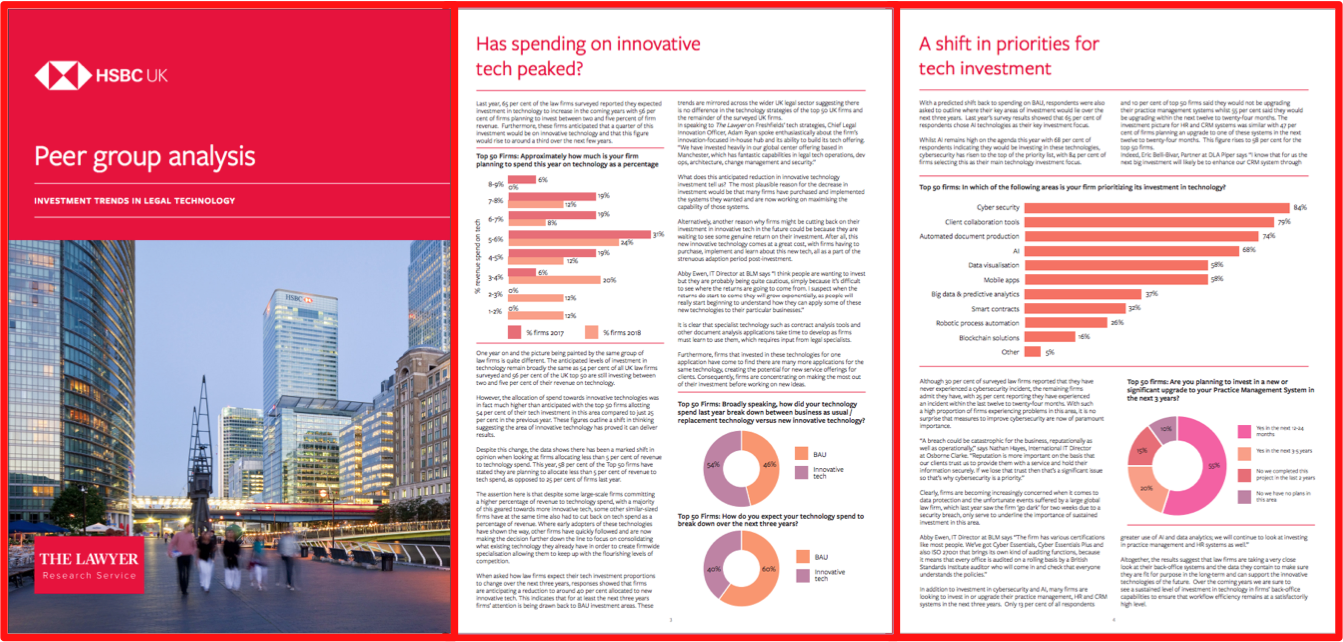














































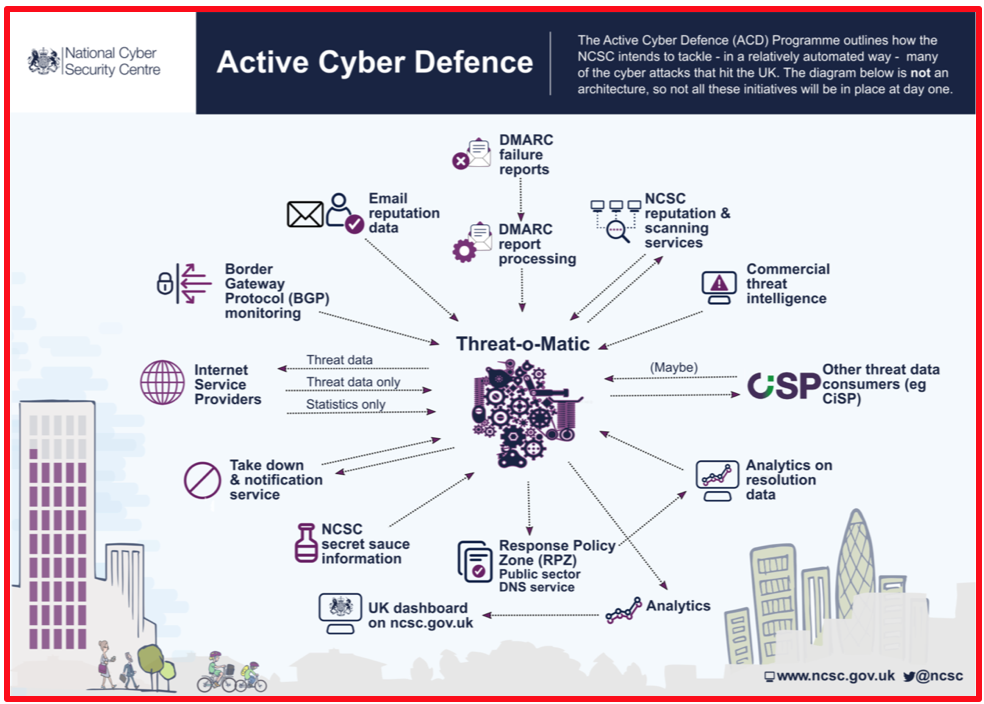



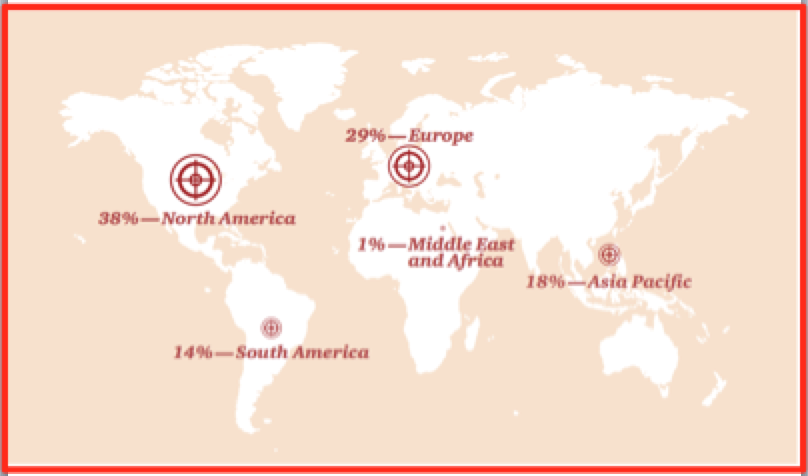


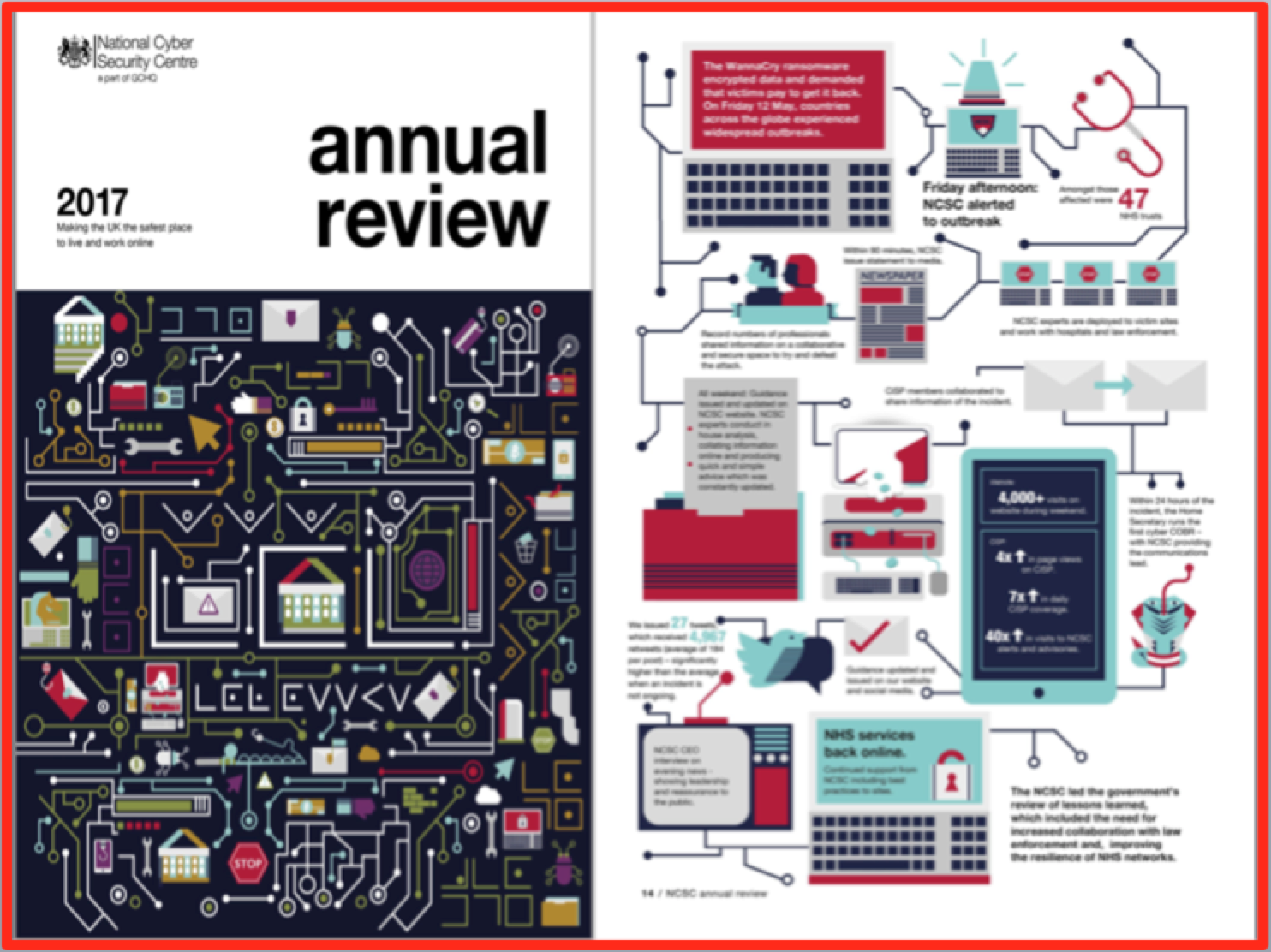





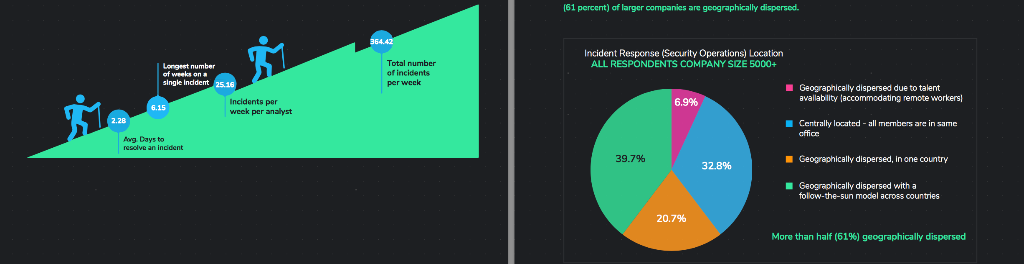

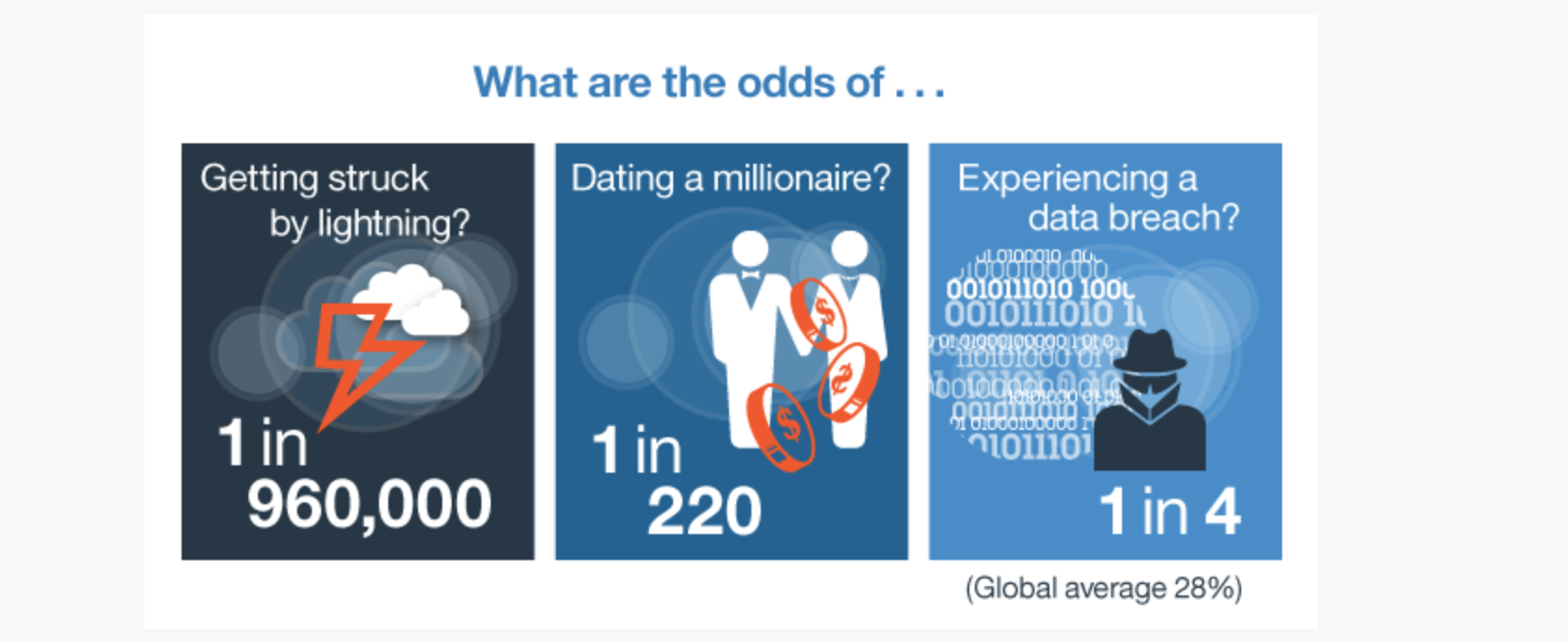
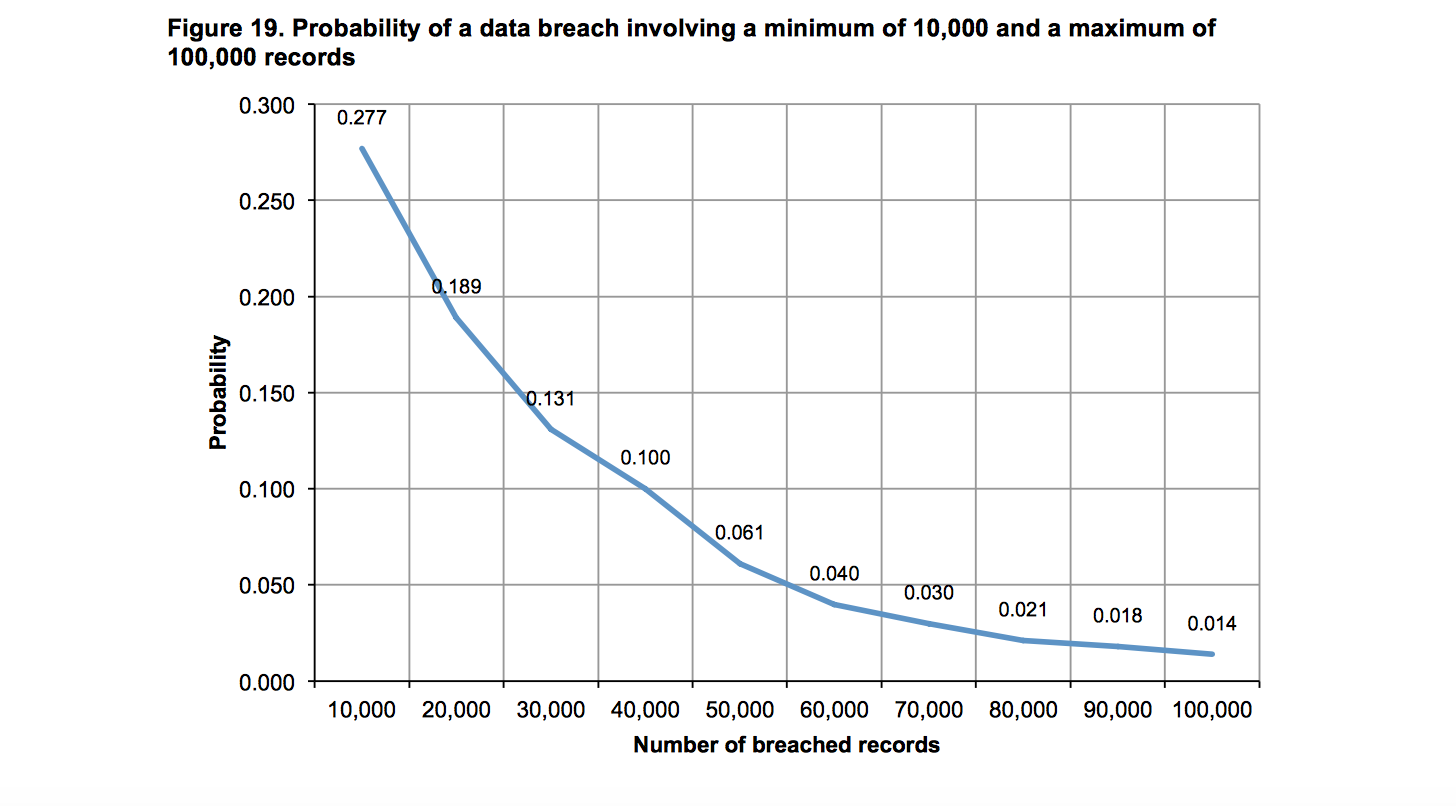
















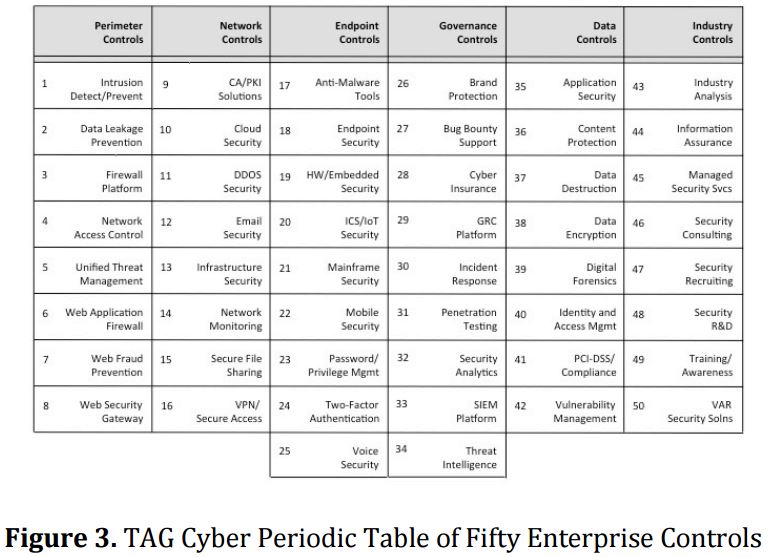




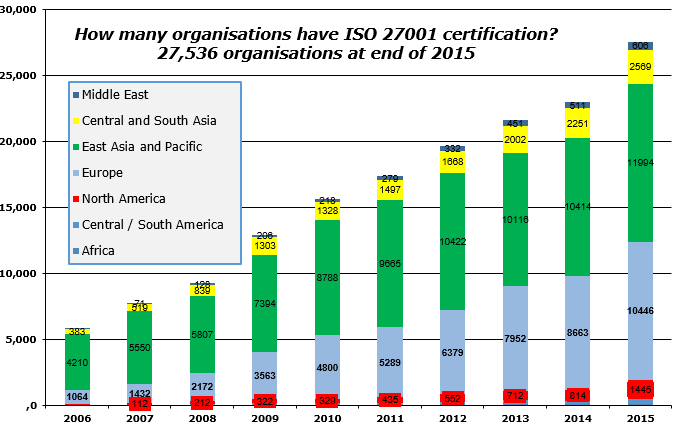




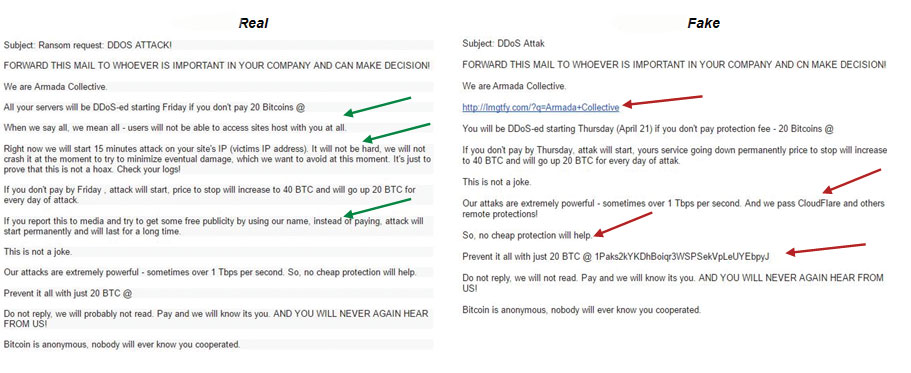
























Membership gives unlimited access to the Cyber Rescue curated library of expert advice on cyber attacks, including: