

































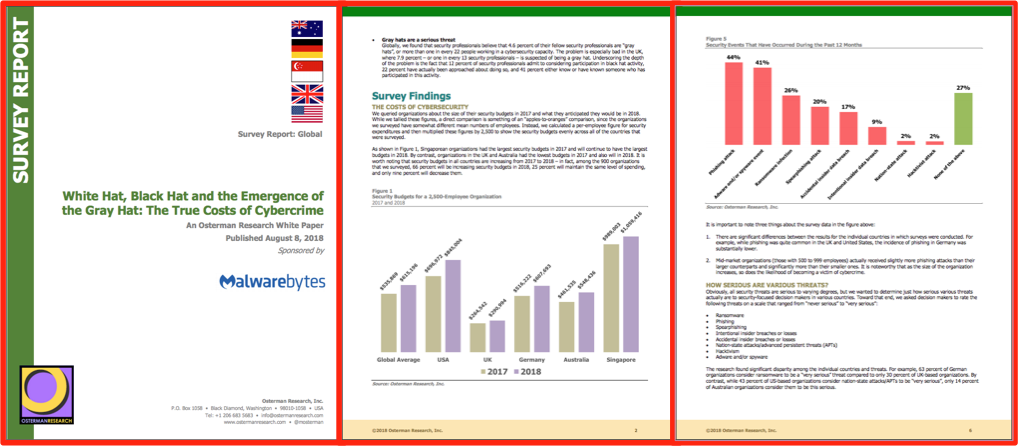

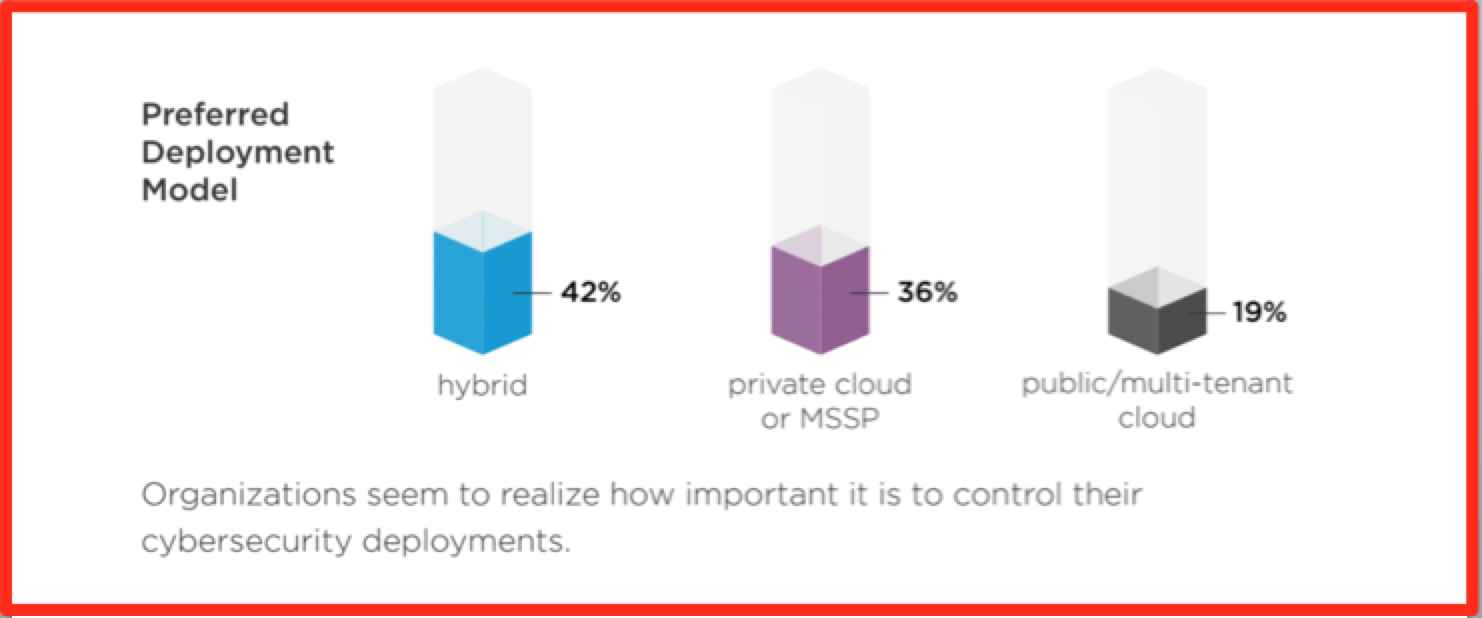
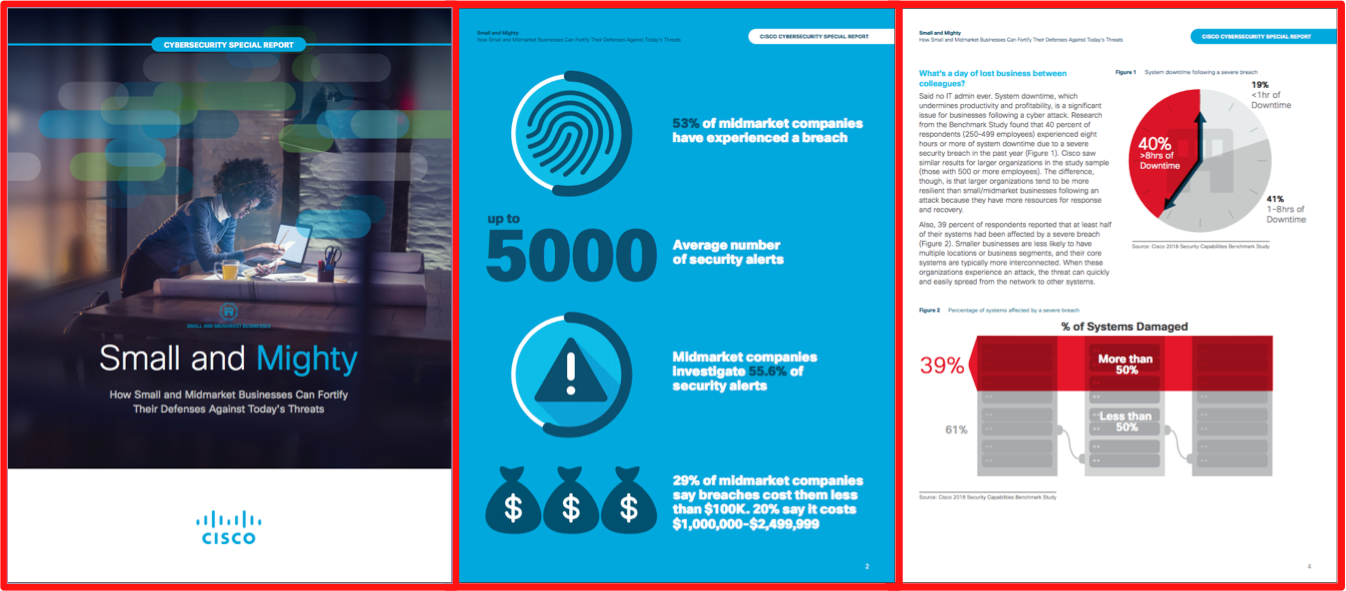
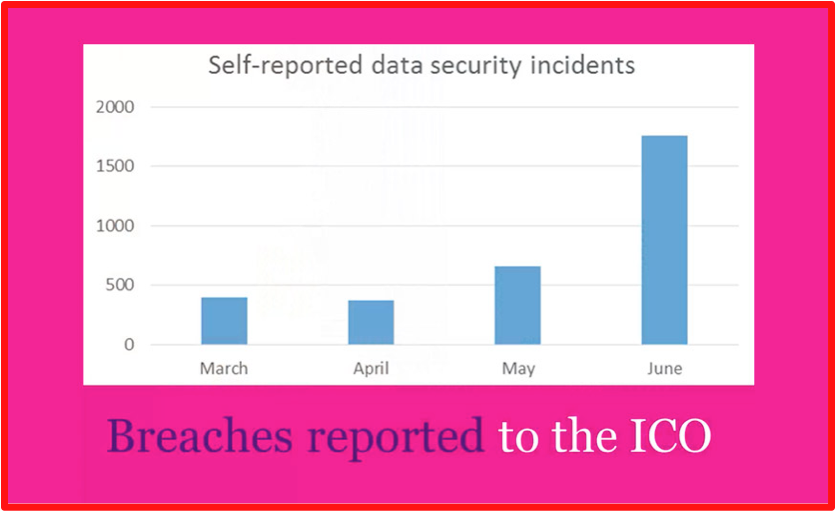
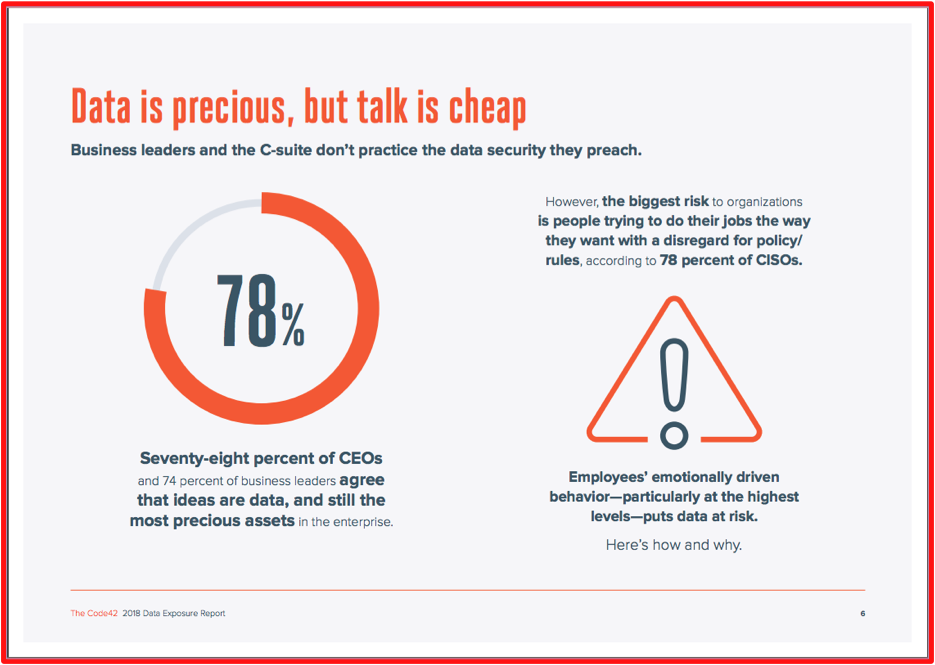

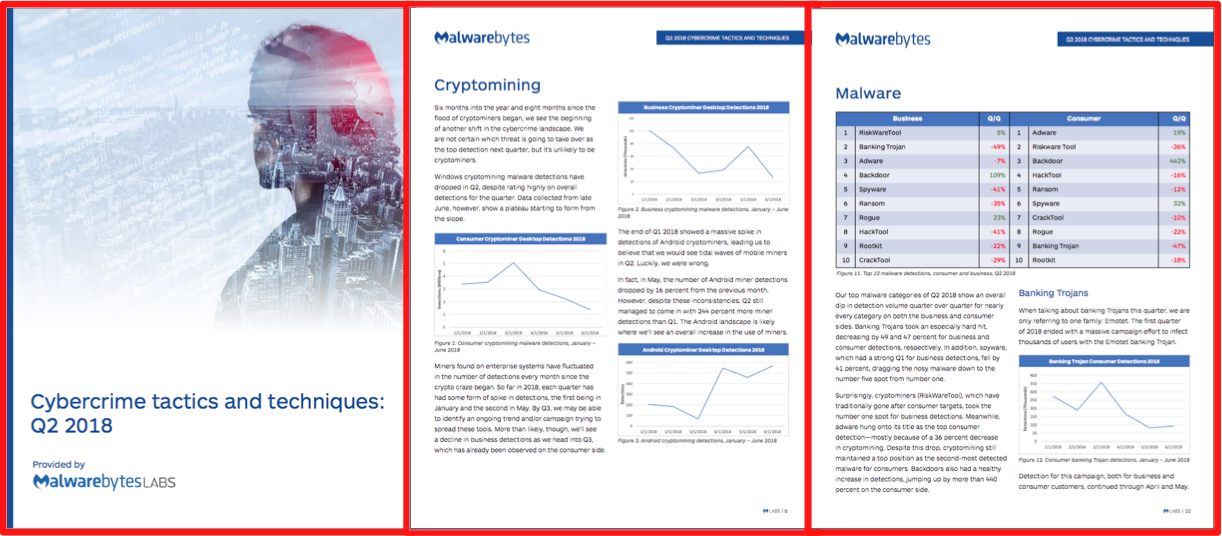







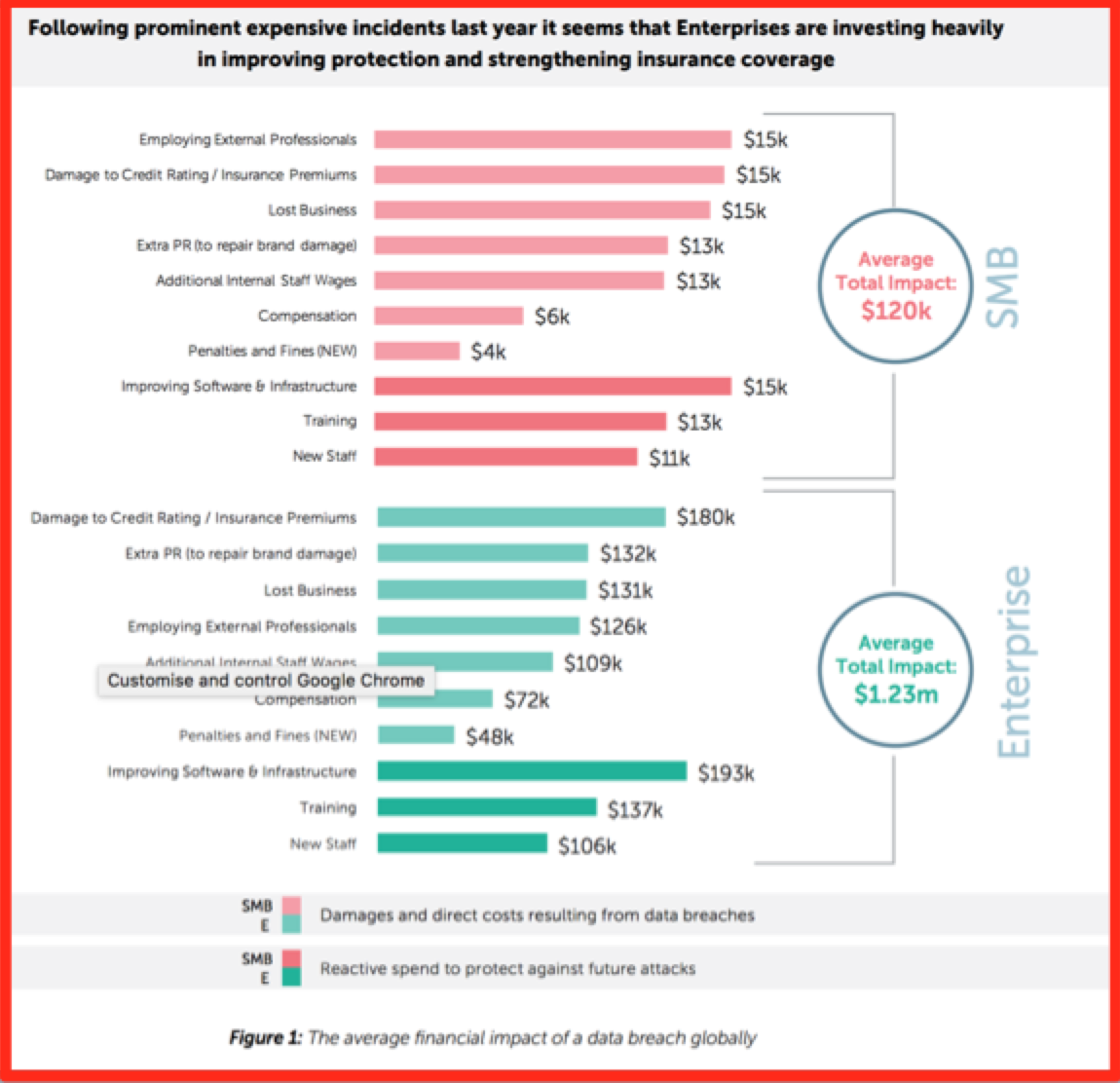

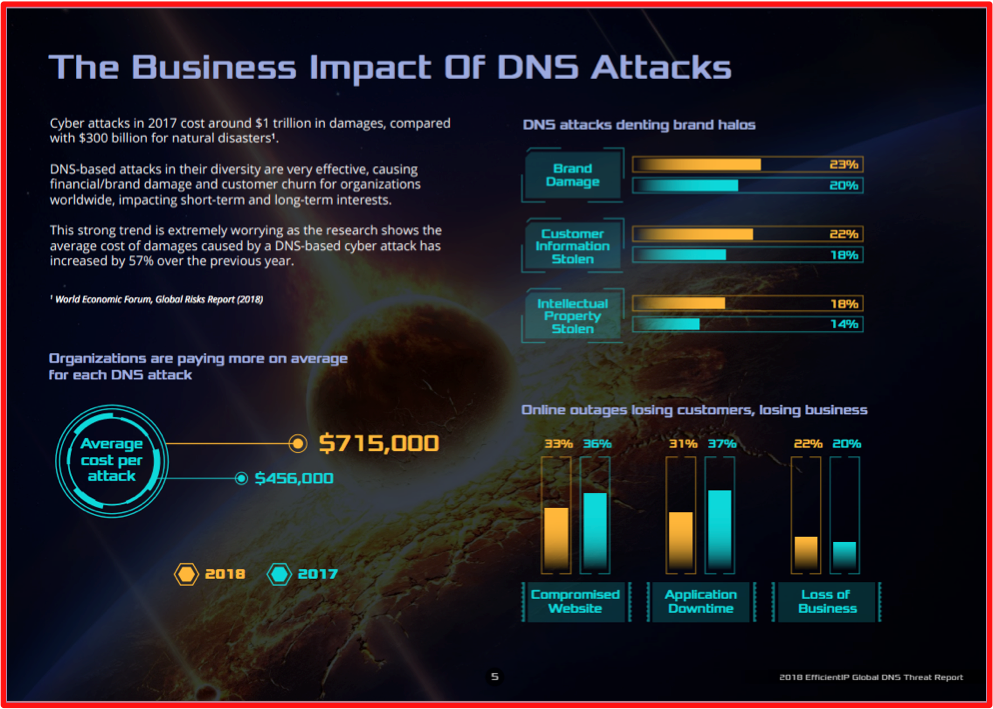




















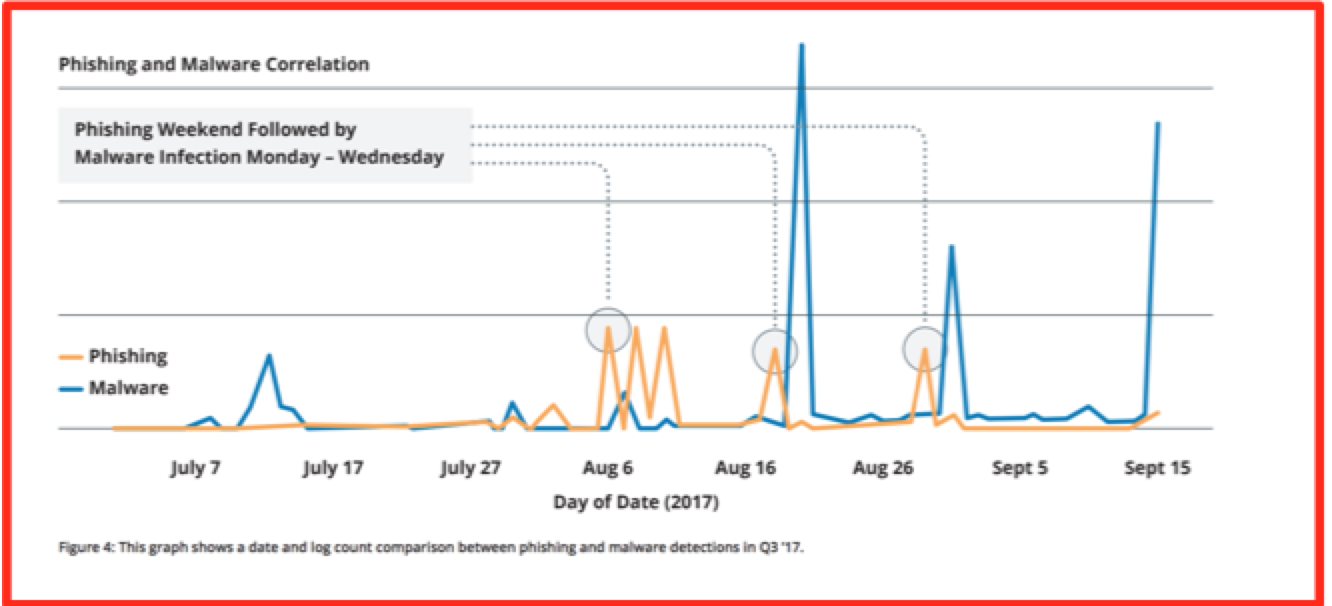






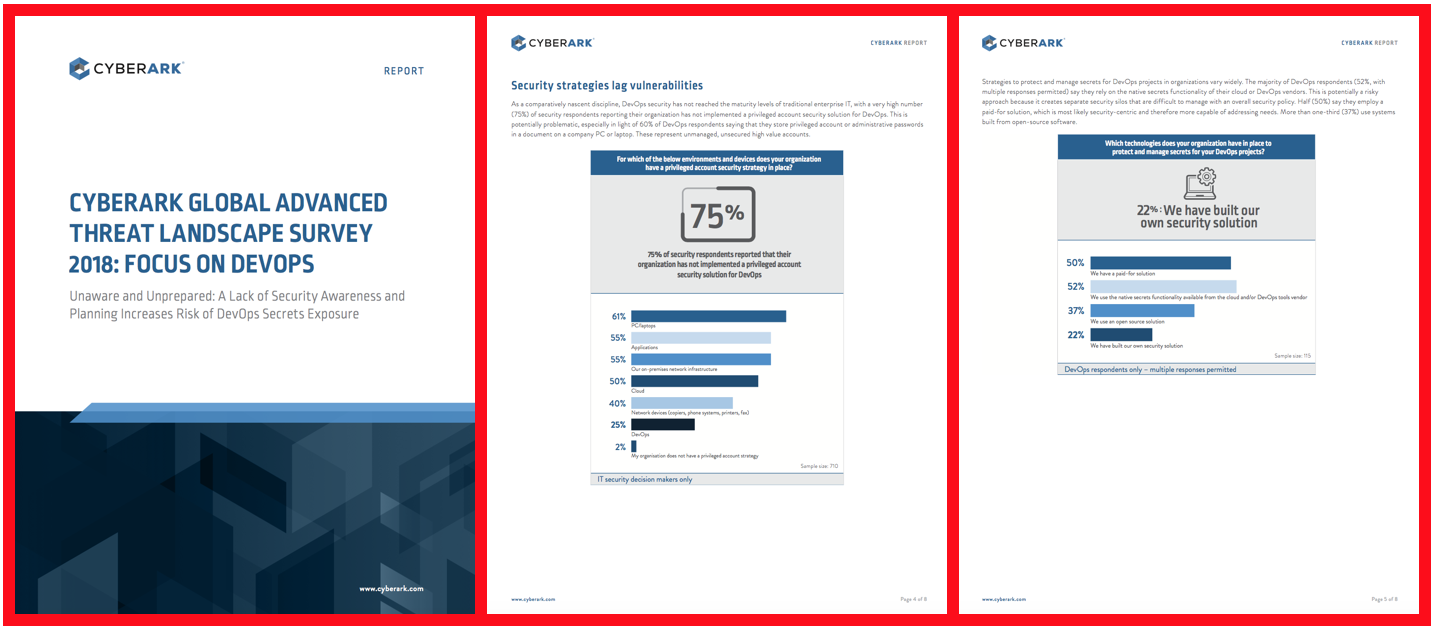
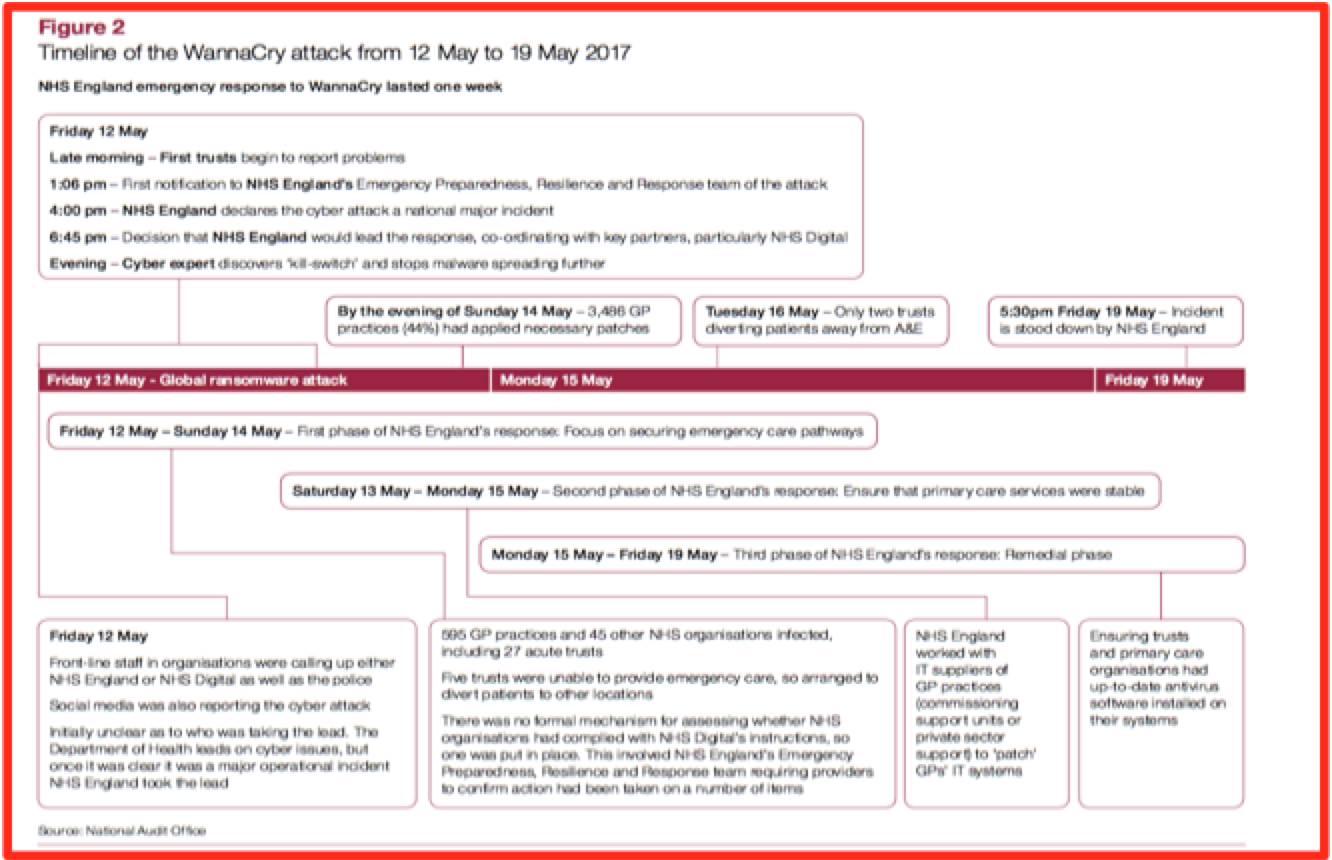








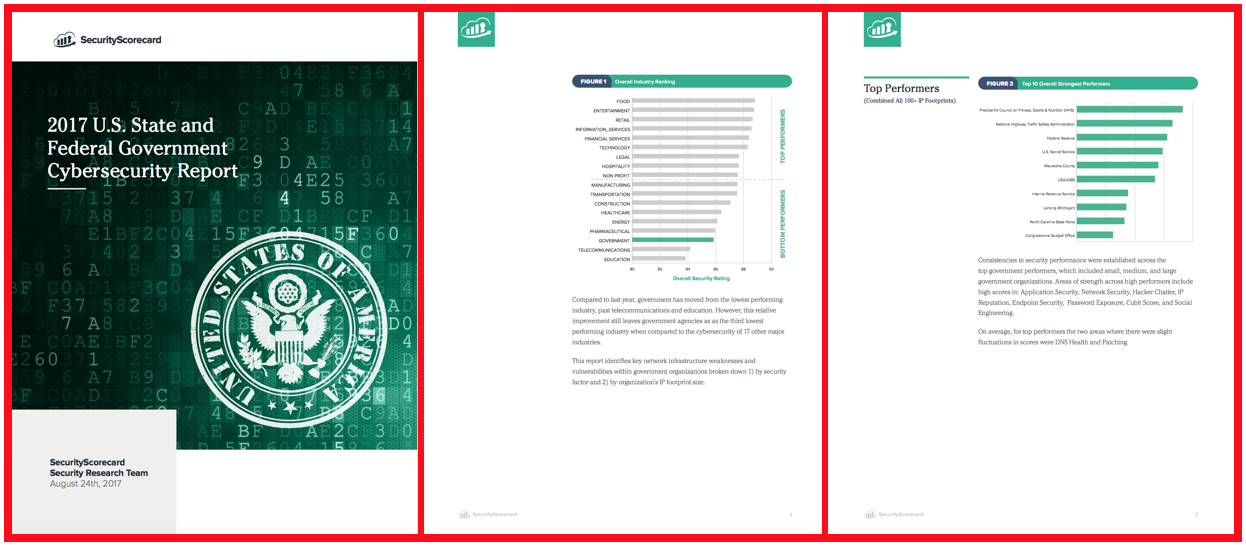





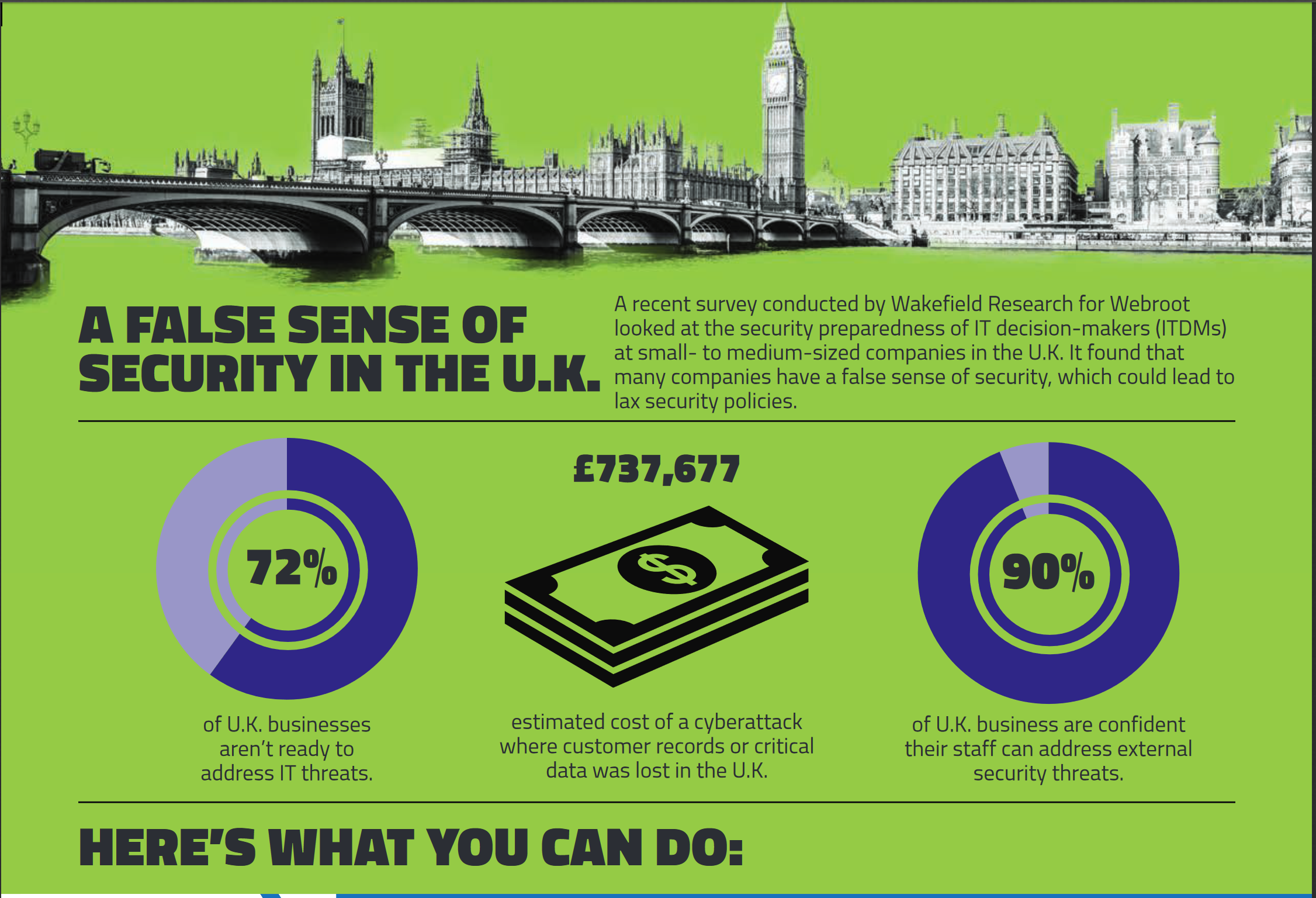


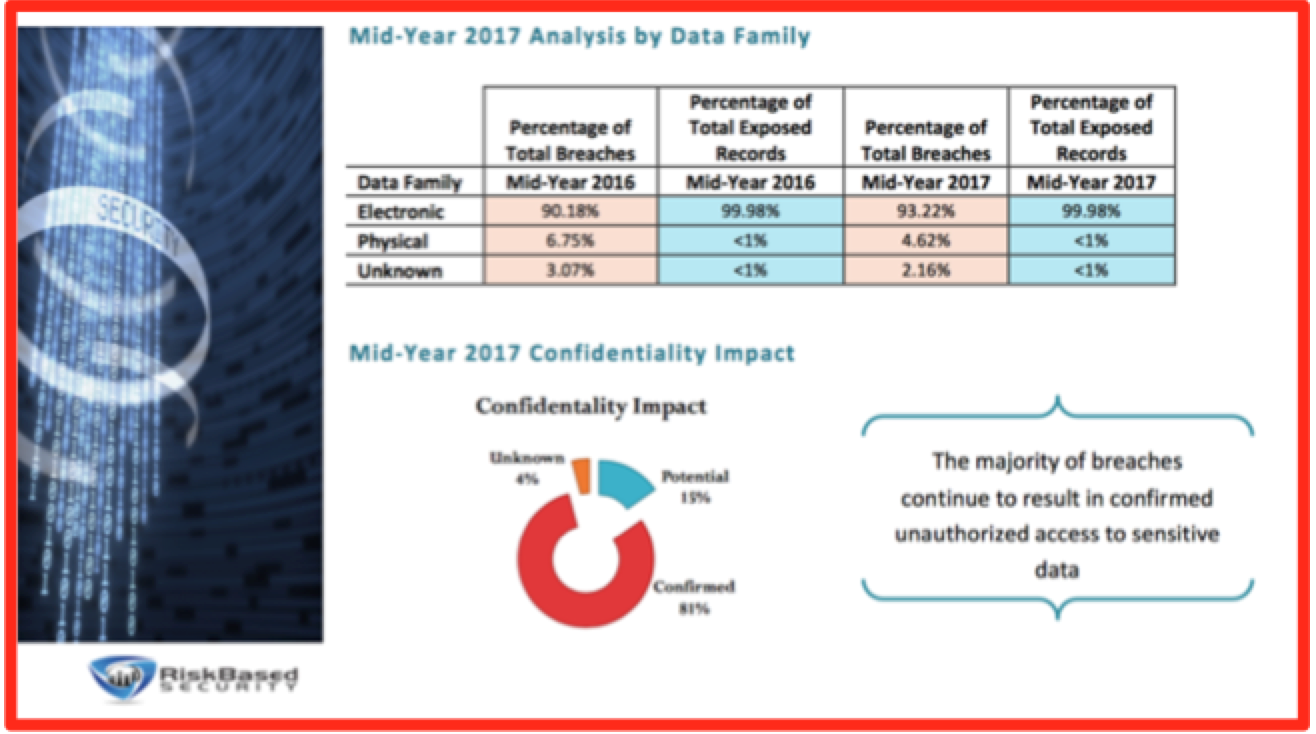
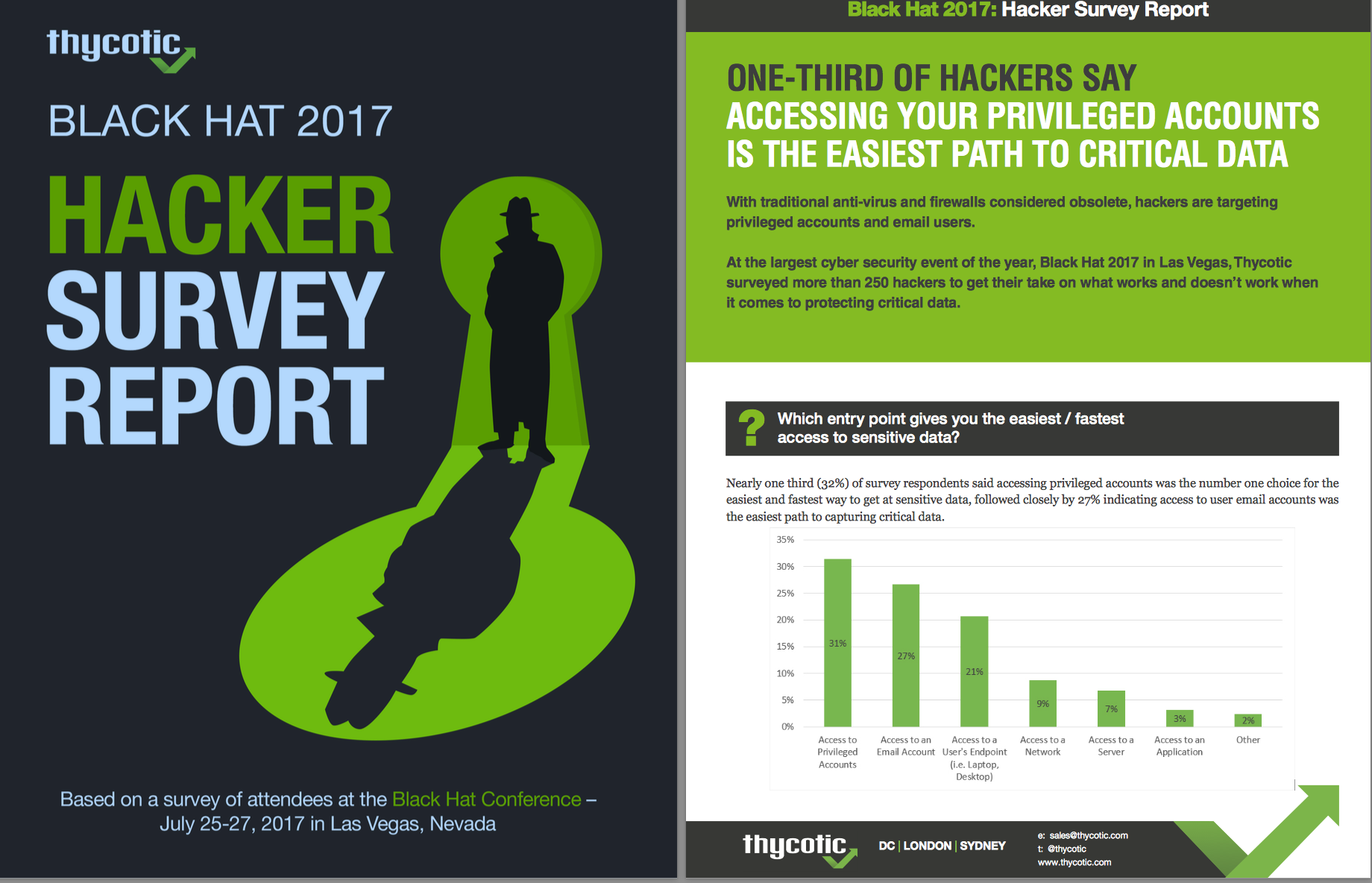


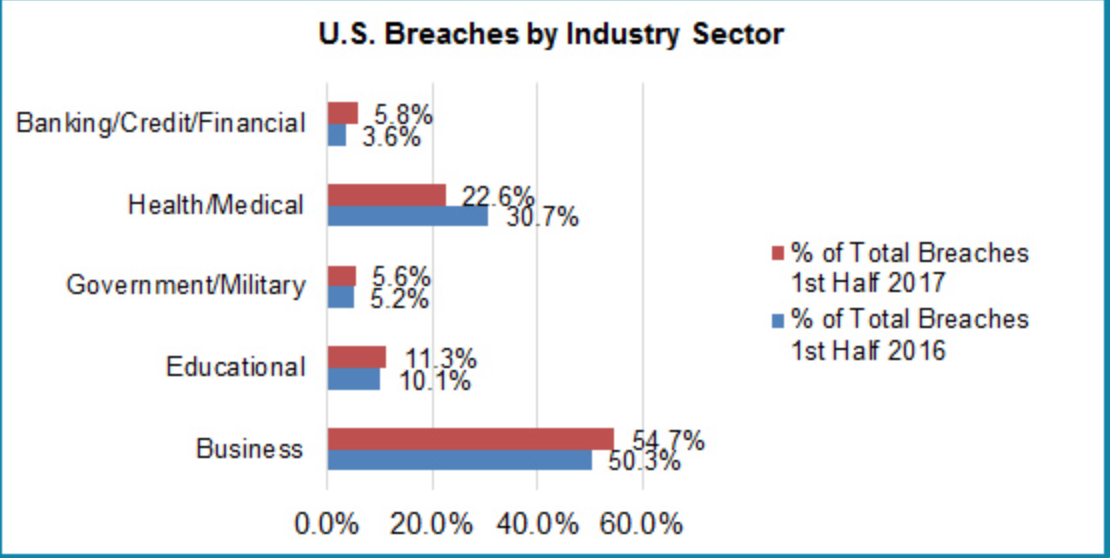























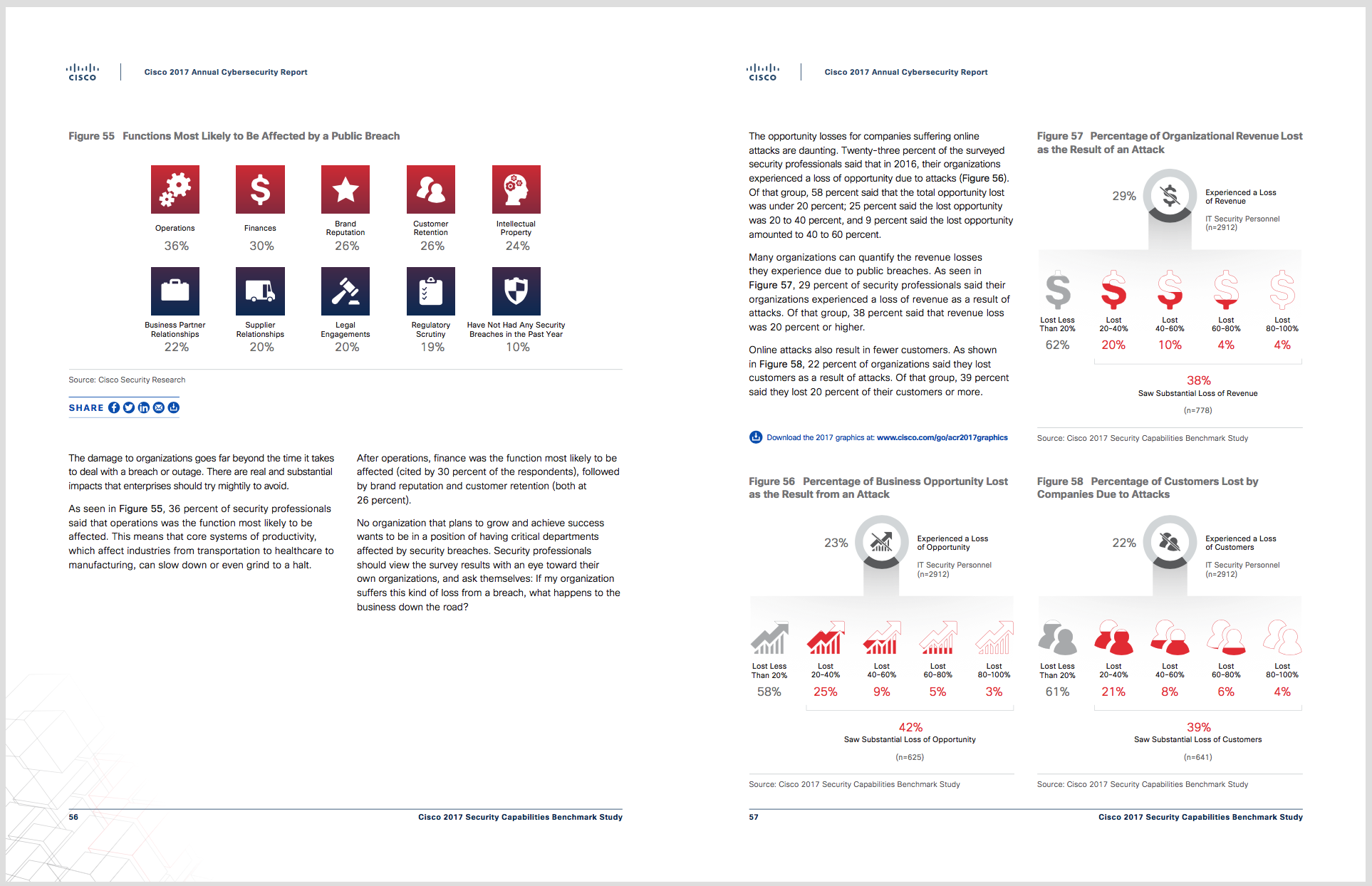
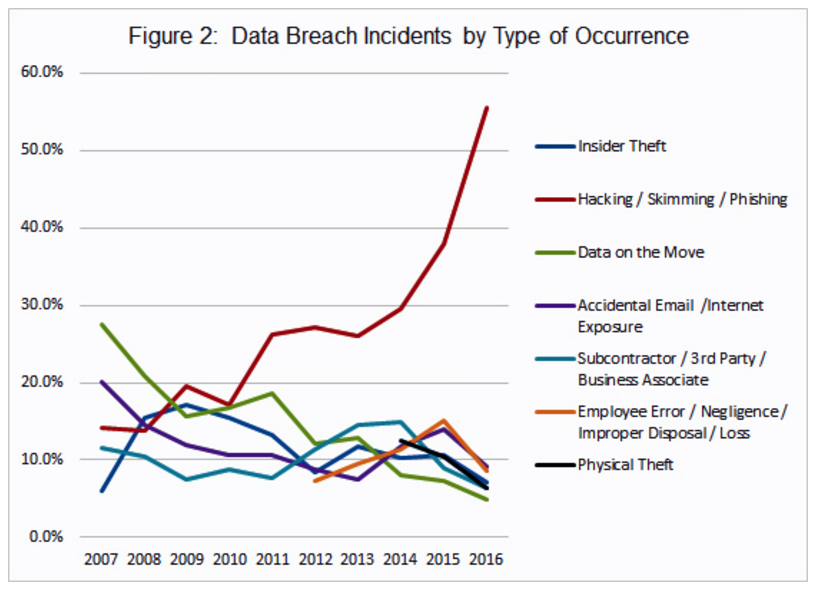
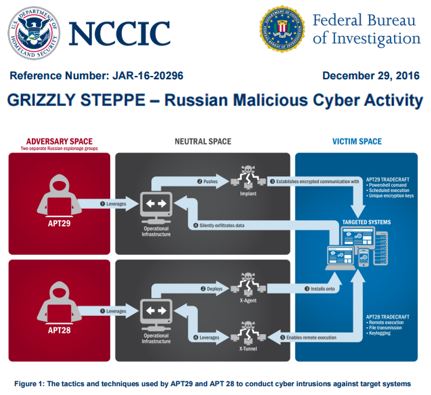
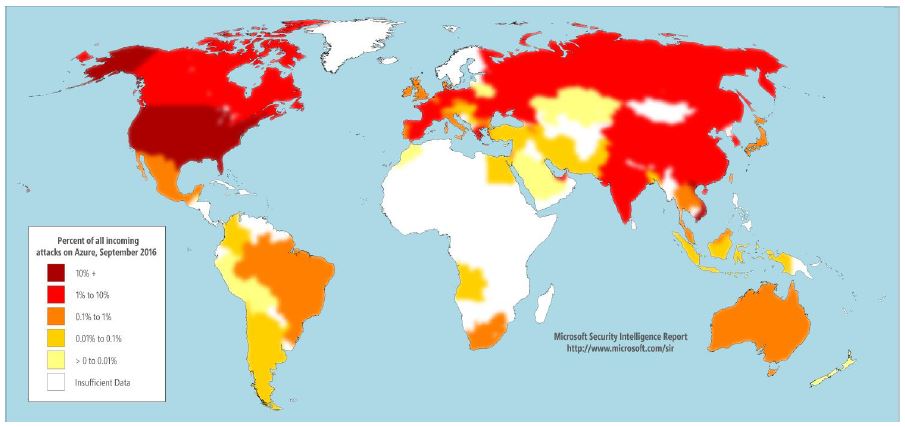

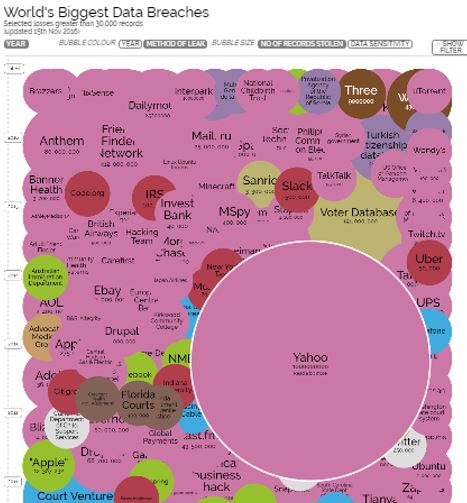




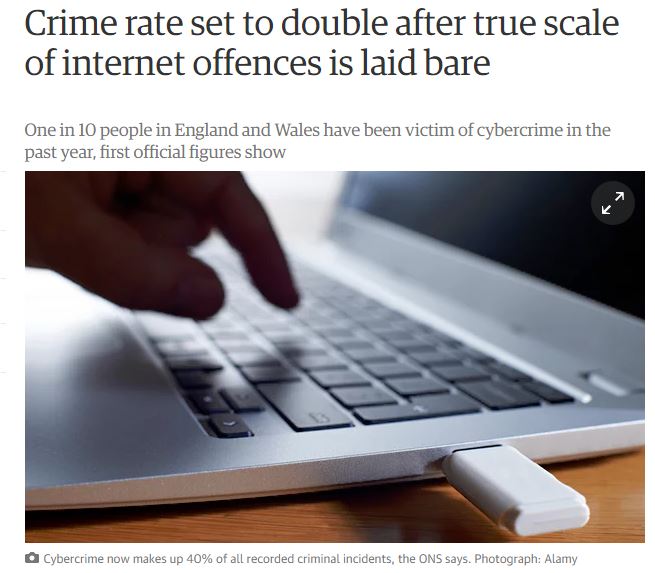
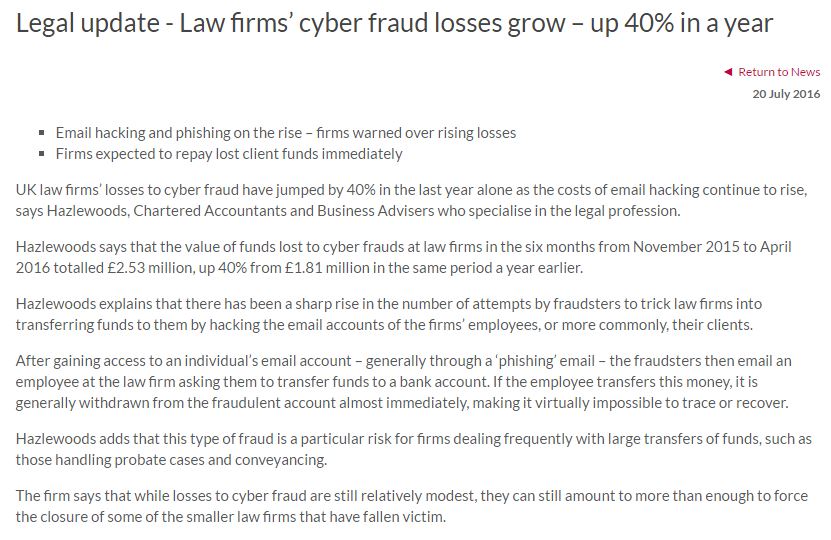









































Membership gives unlimited access to the Cyber Rescue curated library of expert advice on cyber attacks, including:
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Curabitur pharetra dapibus pharetra. Donec interdum eros eu turpis pharetra et hendrerit est ornare. Etiam eu nulla sapien. Nullam ultricies posuere nunc, eget mollis nulla malesuada quis.